The UK has been proposing the notion of backdoors in the encryption used by popular online services which offer end-to-end encryption, such as WhatsApp, iMessage and Snapchat. These proposals go as far back as 2015. In July 2019, the Five Eyes nations proposed similar measures. This went quiet for a while until October 2020 when calls these proposals were renewed (along with representatives from Japan and India). The representatives released a joint statement. On the face of it, the statement seems reasonable. In fact a released PDF of a draft proposal from the EU was made public, which aligns very similarly to the joint PDF from the Five Eyes nations. So, what is all the fuss?
Encryption
Firstly, one must understand what encryption is and what it does. Assuming a user wants to send a message to a family member. This is transmitted over the Internet, through the service provider and finally delivered to that family member:
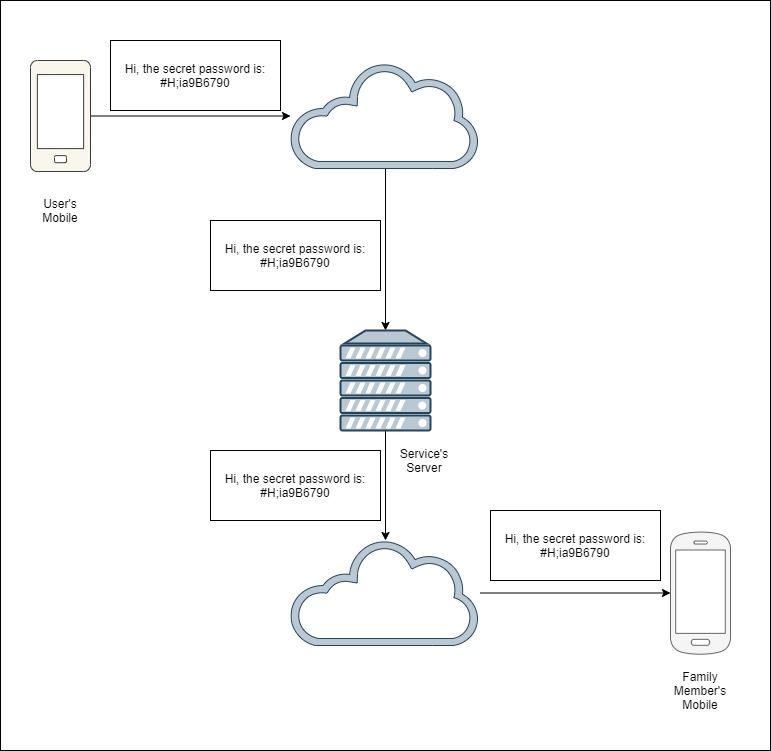
In the diagram above, it is assumed that no end-to-end encryption is used. This means that at any point along the transmission of the message (outside of encrypted communication channels), it is possible for someone, who was not the intended recipient of the message , to be able to read the message:
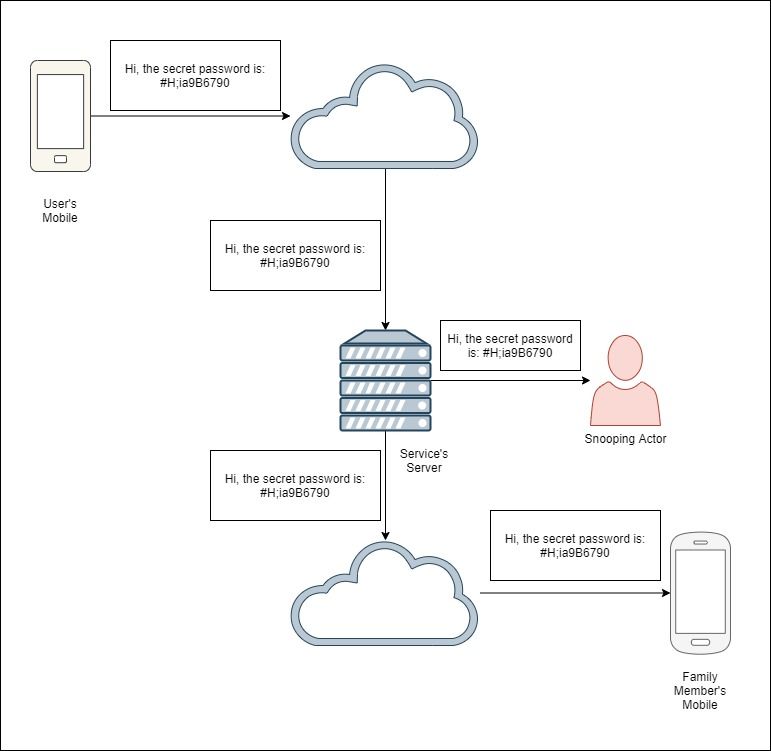
As can be seen in the diagram, anyone with appropriate access (depicted by "Snooping Actor", who could be anyone from an employee at the service, to an attacker who has breached the service, to law enforcement) to the server is able to read the contents of the message (as well as being able to modify the contents of the message). Encryption is the process of encrypting data, using a private encryption key, so that the contents of the original input (called plain text) cannot be derived from the output (called cipher text). End-to-end encryption solves the issue above since the message is encrypted on the user's device and only decrypted on the recipient's device. The secret key is only available to the 2 devices as well:
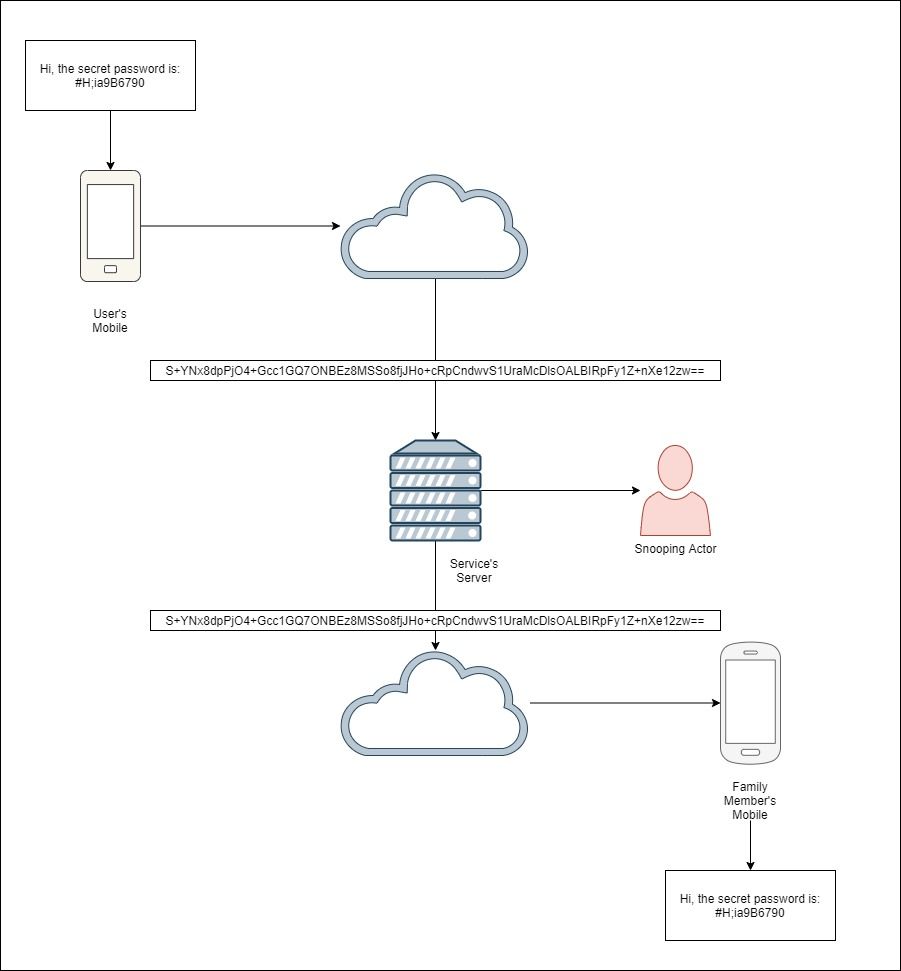
In the example above, the device encrypts the user's message using the encryption algorithm AES-256, with a secret key of SuperSecret. The result is then Base-64 encoded to allow it to be easily transmitted. The family members device uses this same key to then decrypt this message. Since only these 2 devices know this key, anyone else attempting to view the message will seem a jumble of text.
Privacy & Security
Now encryption plays a fundamental part of our everyday lives. We use this daily in a interaction with other systems to do both securely, as well as to protect our own privacy. Take your online banking service, you certainly would not want anyone to be able to view your login credentials (security) and your personal banking records (privacy). Thus, encryption plays a vital role in our everyday lives, so much so that it often becomes an afterthought. With the rise of encryption (and hopefully security) as a default (we see this with the rise of the adoption of HTTPS) it become less and less obvious how important encryption is to both our security as well as privacy.
The Proposals
On the face of it, I can understand why the proposals are being tabled. Criminals will no doubt be making great use of encryption to hide their criminal activities, both to help them carry out criminal acts as well as preventing prosecution against them. However I do have concerns that if we do put some type of mechanism into place which would allow law enforcement to be able to read this private data, it may jeopardise legitimate use of encryption for ordinary law abiding citizens. Currently, to the best of my knowledge, there is no technology which would allow for a secure means of effectively gaining the contents of an encrypted message. The only thing which could be a possibility is the use of public key encryption. But this on its own carries significant risk. The decryption key still must be held outside of the intended recipients.
The Questions
So, based off the proposals I would have this initial set of questions:
- If public key encryption is used:
- How is the private key protected?
- Who has access to this private key, and how do they gain access to it?
- What happens when they have finished with this private key?
- What happens if this key is lost or stolen?
- Who controls this key?
- What if public key encryption is not suitable, what will be used then?
- How do we prevent this practice/proposal from being abused?
- What happens when the criminals simply move off onto a platform with no encryption "backdoors"?
- How do we ensure that oppresive regimes don't start using this to spy on their citizens?
Conclusions
So, while I do see the request and desire for what is being proposed, I simply fail to see it being implemented securely in practice. In my opinion there is simply too much at stake. Ultimately this will not be my decision to make, and I accept that. But I do want to ensure that the appropriate questions are being asked, and that they are in fact dealt with. This is one of the reasons why I have created an official petition against the proposals:

The intent of the petition is to ensure that the appropriate questions are asked, that a debate is had around the proposals and that they are simply not blindly implemented.
A side note on the EU proposals, back in June 2017, the EU sought to outlaw the proposed "backdoors" from the UK.



