A few months back I bought myself a WiFi Pineapple and had some issues trying to get it setup for a Man in The Middle scenario with a proxy. Initially I looked online and did not really come across anything. Some people simply configure their browser's proxy to point to the WiFi Pineapple, which kind of defeats the purpose of a Man in The Middle demonstration. This post will provide a guide as how to do this, and hopefully save yourselves some time.
DISCLAIMER - these instructions are only meant for educational purposes and should under no circumstances be used to help or carry out illegal activities.
Setup DNS
This section only applies if you are using Dnsmasq to resolve your DNS queries. One thing that I had spent ages trying to get working for this was DNS. For some reason, when a MASQUERADE iptables rule is used, Dnsmasq is not happy and no DNS names resolve. This is obviously an issue for trying to covertly pull off a Man in The Middle attack! To solve this, I had to configure Dnsmasq to instead use preconfigured DNS servers.
- Edit the file /etc/resolvconf/resolv.conf.d/head
- Add the following contents (the servers below are the new Cloudflare DNS servers, but you can change these to any DNS servers you would like):
nameserver 1.1.1.1
nameserver 1.0.0.1
- Update the config:
sudo resolvconf -u
- Restart your network manager to allow the new settings to take affect:
sudo service network-manager restart
Setup Wifi Pineapple
The next bit will setup Internet connection sharing with your Wifi Pineapple. Run the wp6.sh script to setup the Internet connection sharing with the Pineapple:
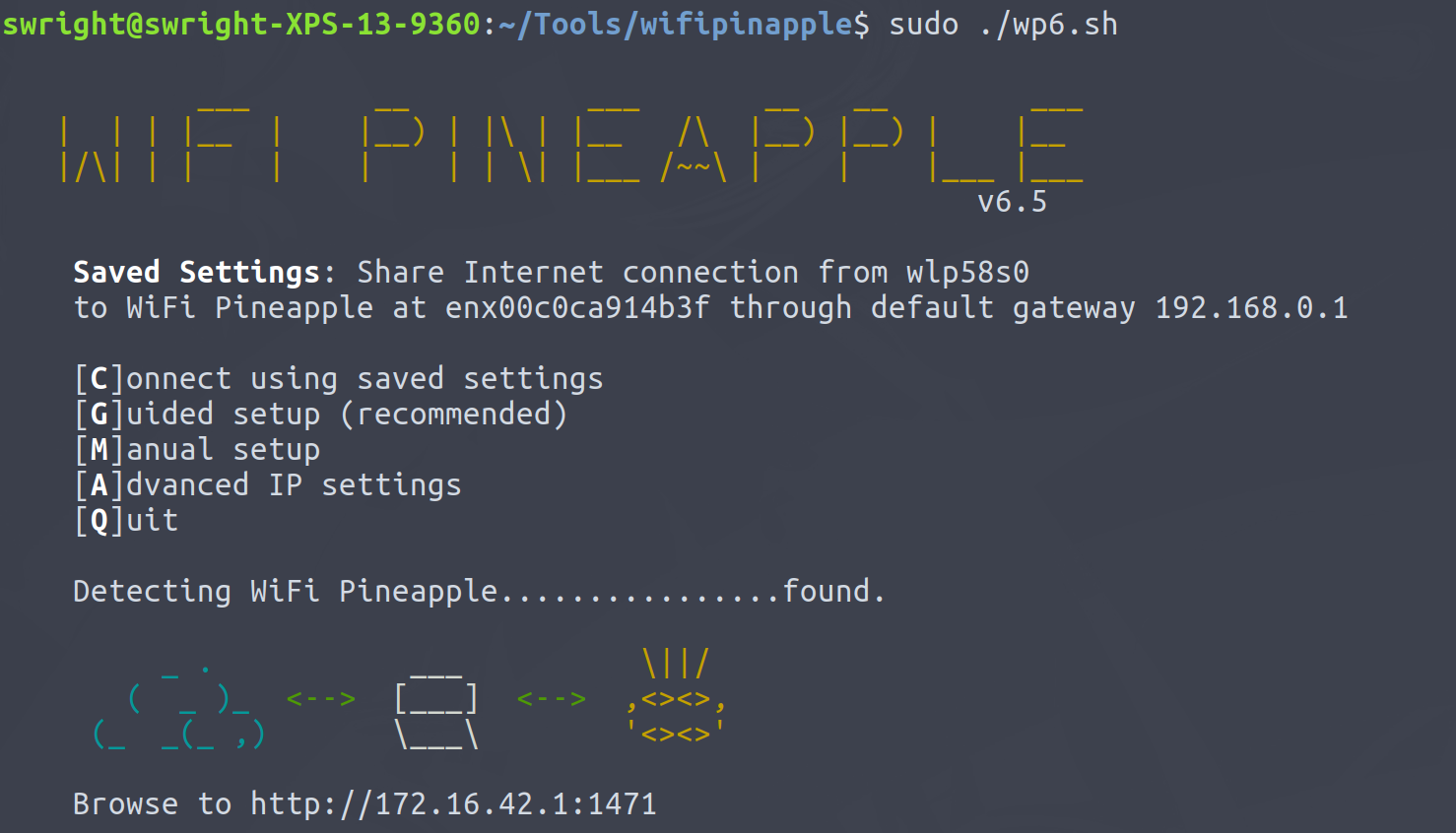
Once you have the Pineapple configured, log into the web admin interface using the address from the script.
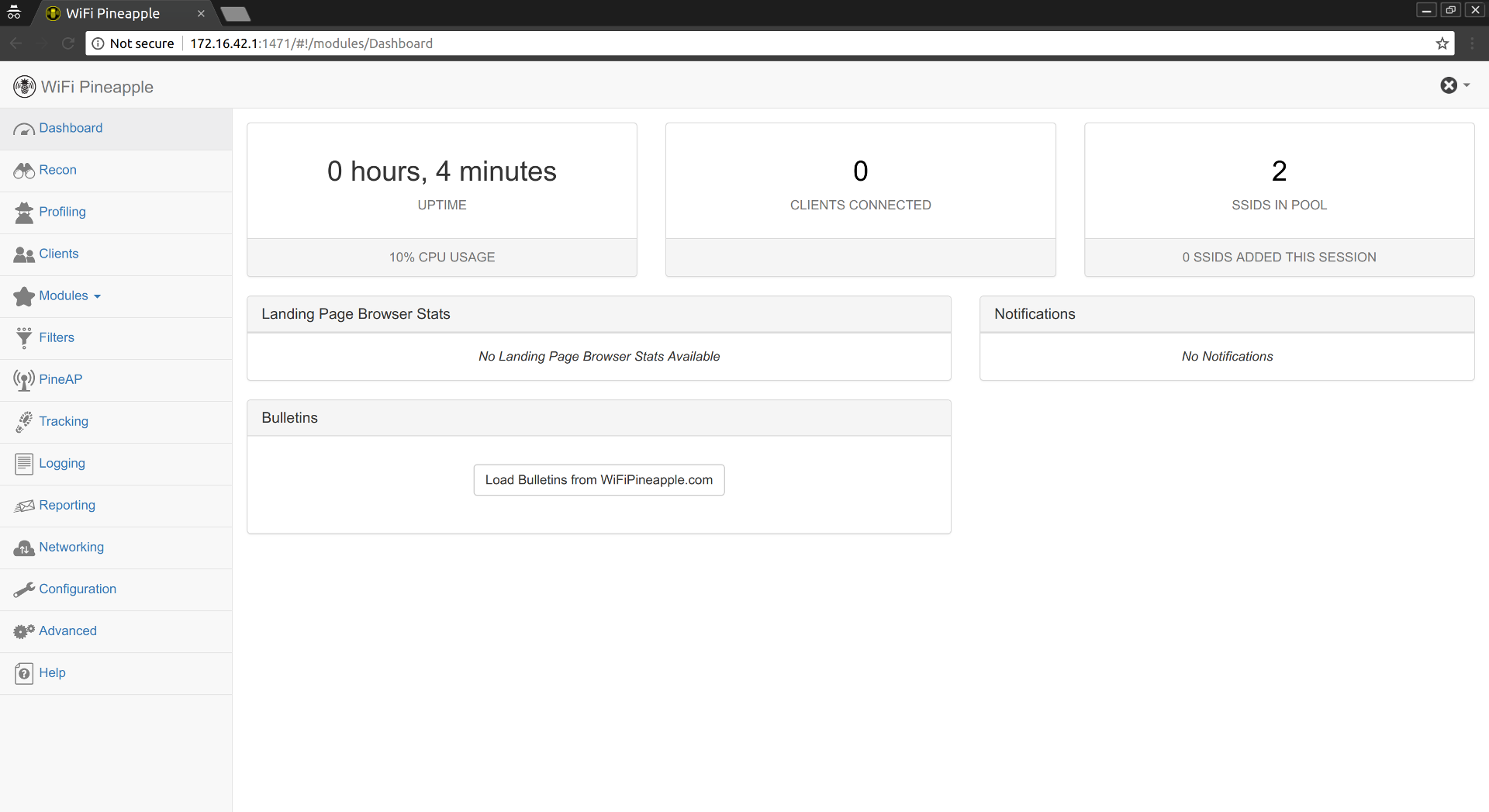
The next step is to configure the "rogue" access points:
- Navigate to PineAP in the web admin interface.
- Click on the Switch button to the right of PineAP Daemon: Disabled.
- Ensure the you enter at least 1 SSID into the SSID Pool.
- Check the following checkboxes
- Allow Associations
- Log PineAP Events
- Beacon Response
- Broadcast SSID Pool
- Click on the Save button.
- Ensure that your "rogue" AP is now available.
Setup BurpSuite
The last bit is to configure BurpSuite. Firstly you will need to redirect traffic on port 80 (HTTP) and port 443 (HTTPS) to go to BurpSuite. To do this add the follow iptable rules:
sudo iptables -t nat -A PREROUTING -p tcp -i <wifi-pineapple-interface> --destination-port 80 -j REDIRECT --to-port 8080
sudo iptables -t nat -A PREROUTING -p tcp -i <wifi-pineapple-interface> --destination-port 443 -j REDIRECT --to-port 8080
Next is to open BurpSuite and perform the following:
- Navigate to the Proxy tab.
- Navigate to the Options sub-tab.
- In the Proxy Listeners section, select the current listener and press the Edit button.
- In the Bind to address field, select Specific address and then select the address of your Wifi Pineapple (this will be the same IP as the IP used in the URL to access the Wifi Pinable web admin interface).
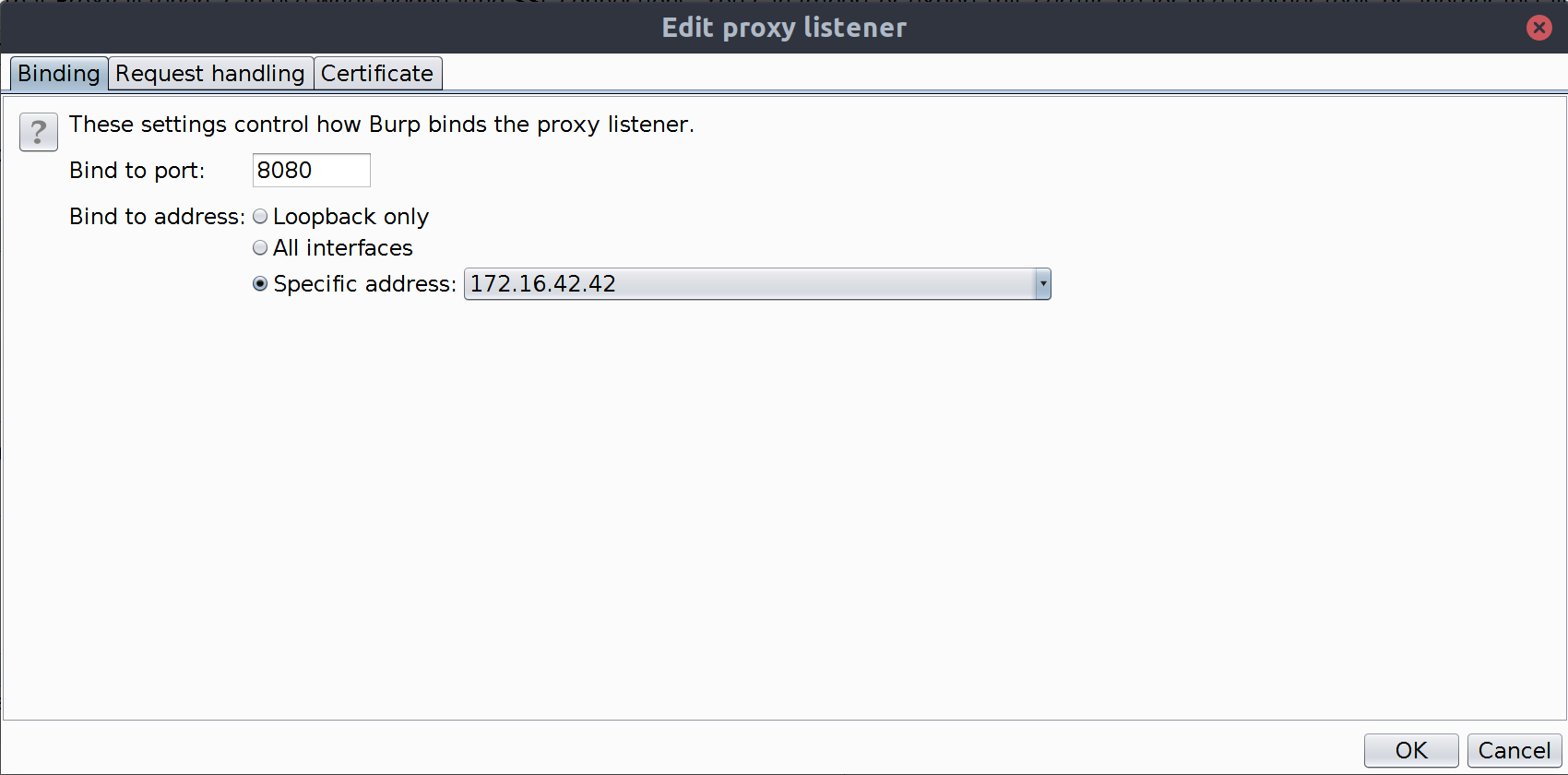
- Select the Request Handling tab.
- Check the checkbox Support invisible proxing.
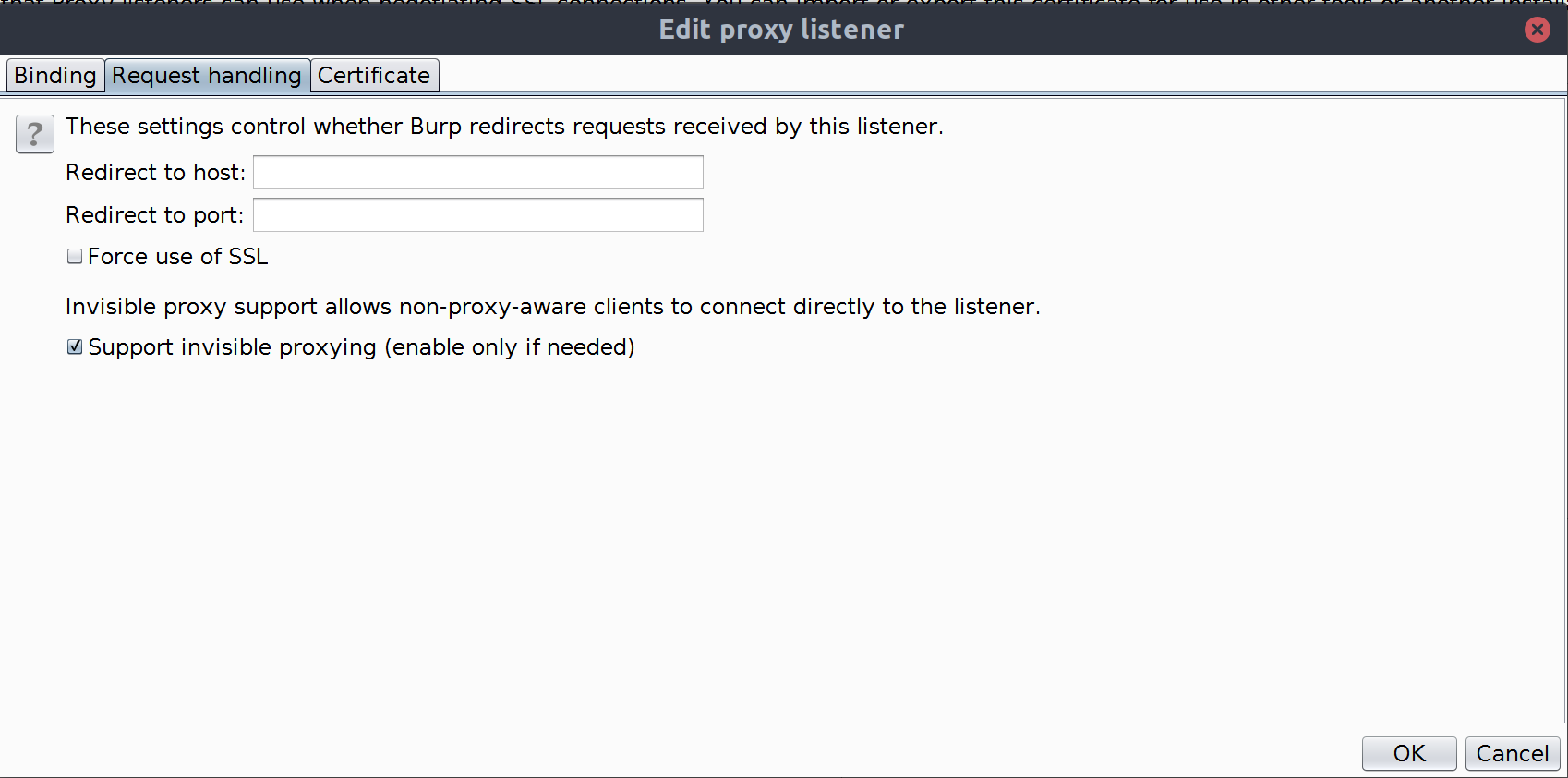
- Click on the OK button.
- Navigate to the Intercept and click on the Intercept is on button.
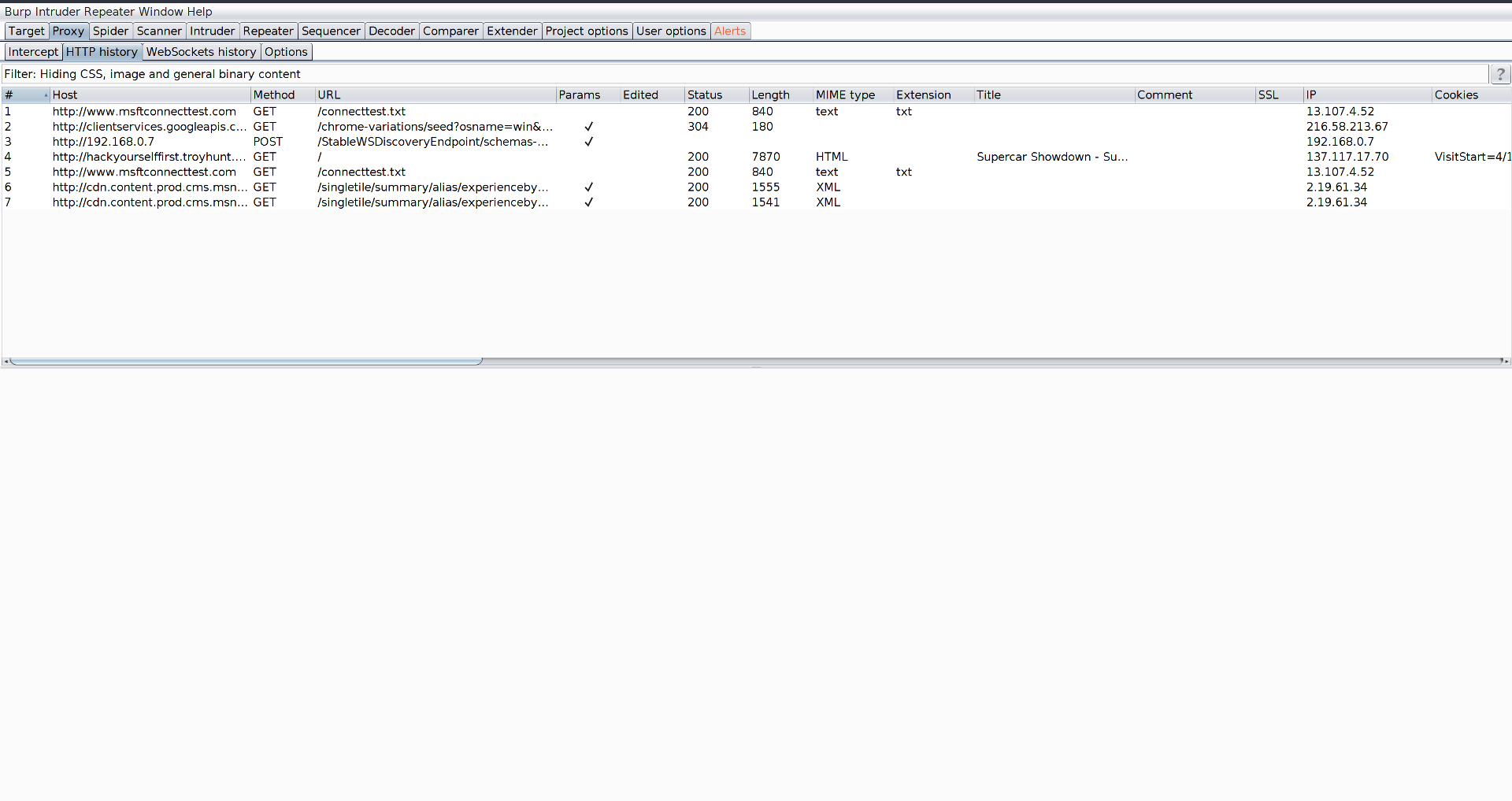
- Navigate to the HTTP history sub-tab.
- Use a client (victim) to connect to the "rogue" AP and navigate to a site.
- In BurpSuite, ensure that it is now receiving the requests from the victim: