Title: Scottish Power - Open Redirect
Date Published: 11 February 2019
CVE: N/A
CVSSv3 Base Score: 9.3 (AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:N)
Vendors Contacted: Scottish Power
Discovered By: Sean Wright
Summary
An Open Redirect exists on the Direct Debit agreement link sent out by Scottish Power to their future customers (as part of the takeover of Extra Energy customers).
Details
Scottish Power recently took over the accounts of Extra Energy clients, after Extra Energy ceased trading. As a result, Scottish Power emailed these clients details of their current Direct Debit orders, along with a link to confirm that the detail are correct.
Below is a screenshot of this email with details of the agreement link:
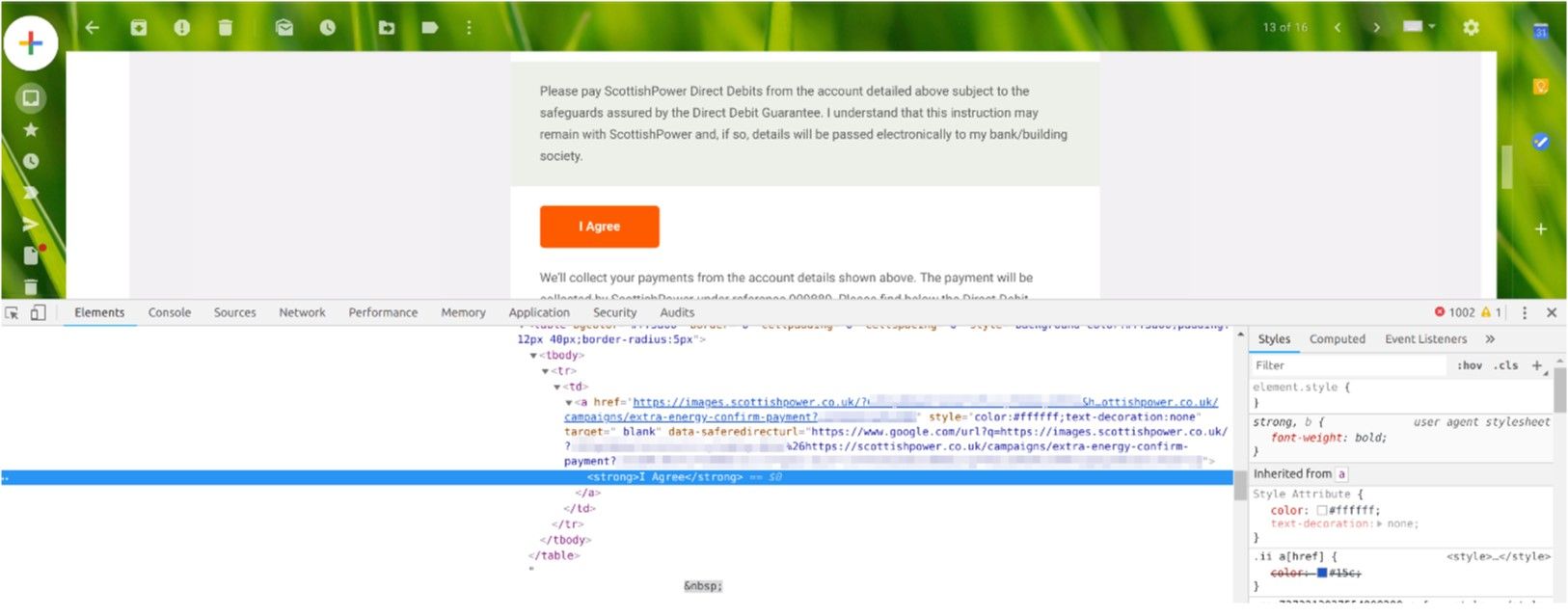
The agreement link takes the form of:
hxxps://images.scottishpower.co.uk/?<token>&<redirect-url>
For example:
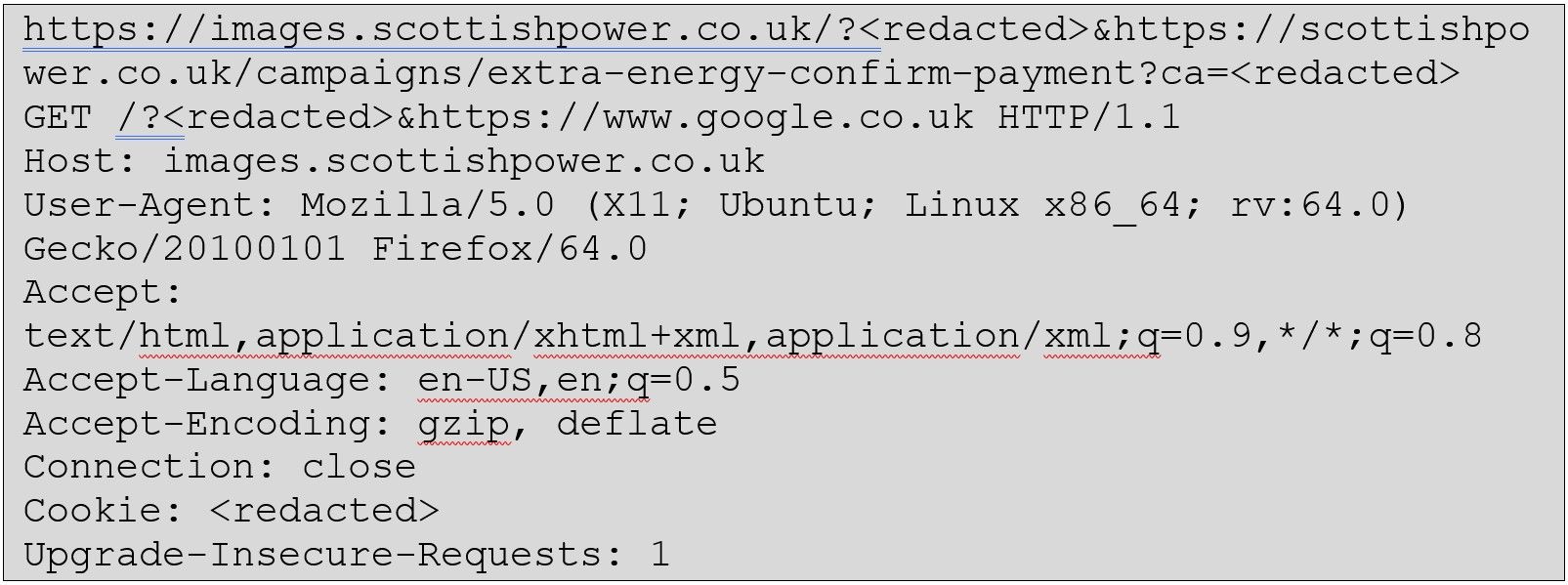
Upon investigation into the request and response of the above link, the response redirects the user to the target URL:
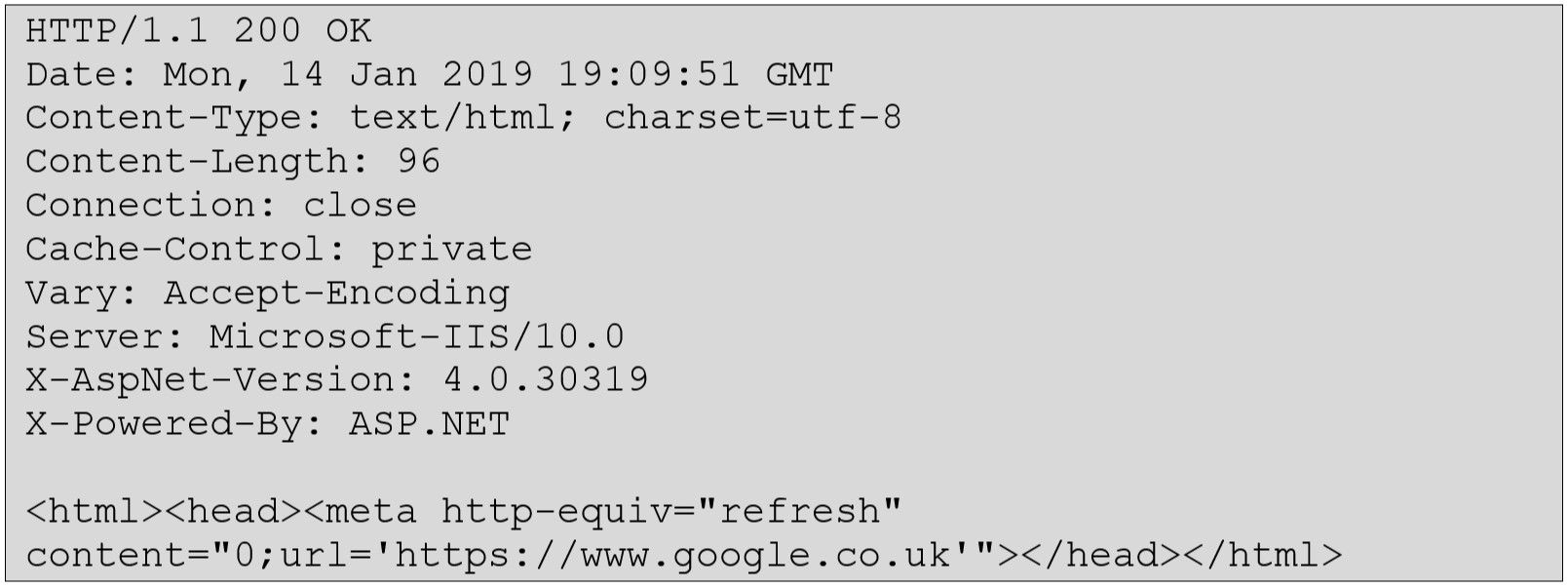
However, it appears that this target URL is never validated, thus an attacker can use this feature to perform malicious actions. Below is a benign example of redirecting a victim to the Google search homepage:
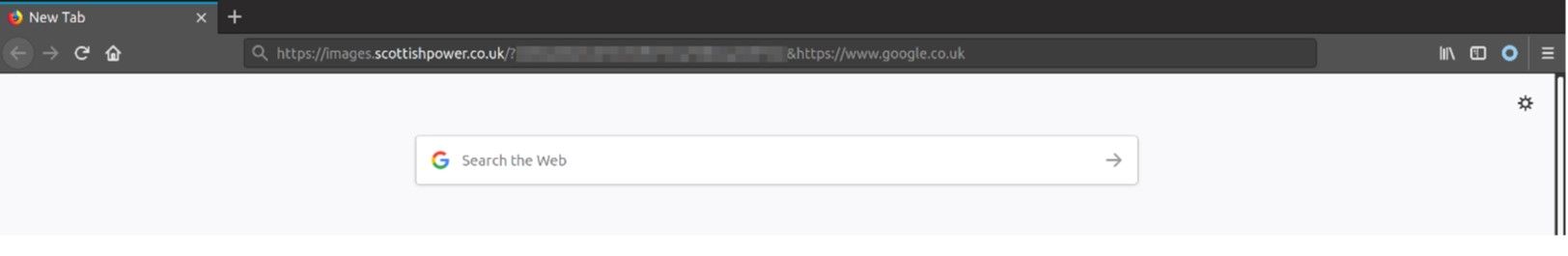
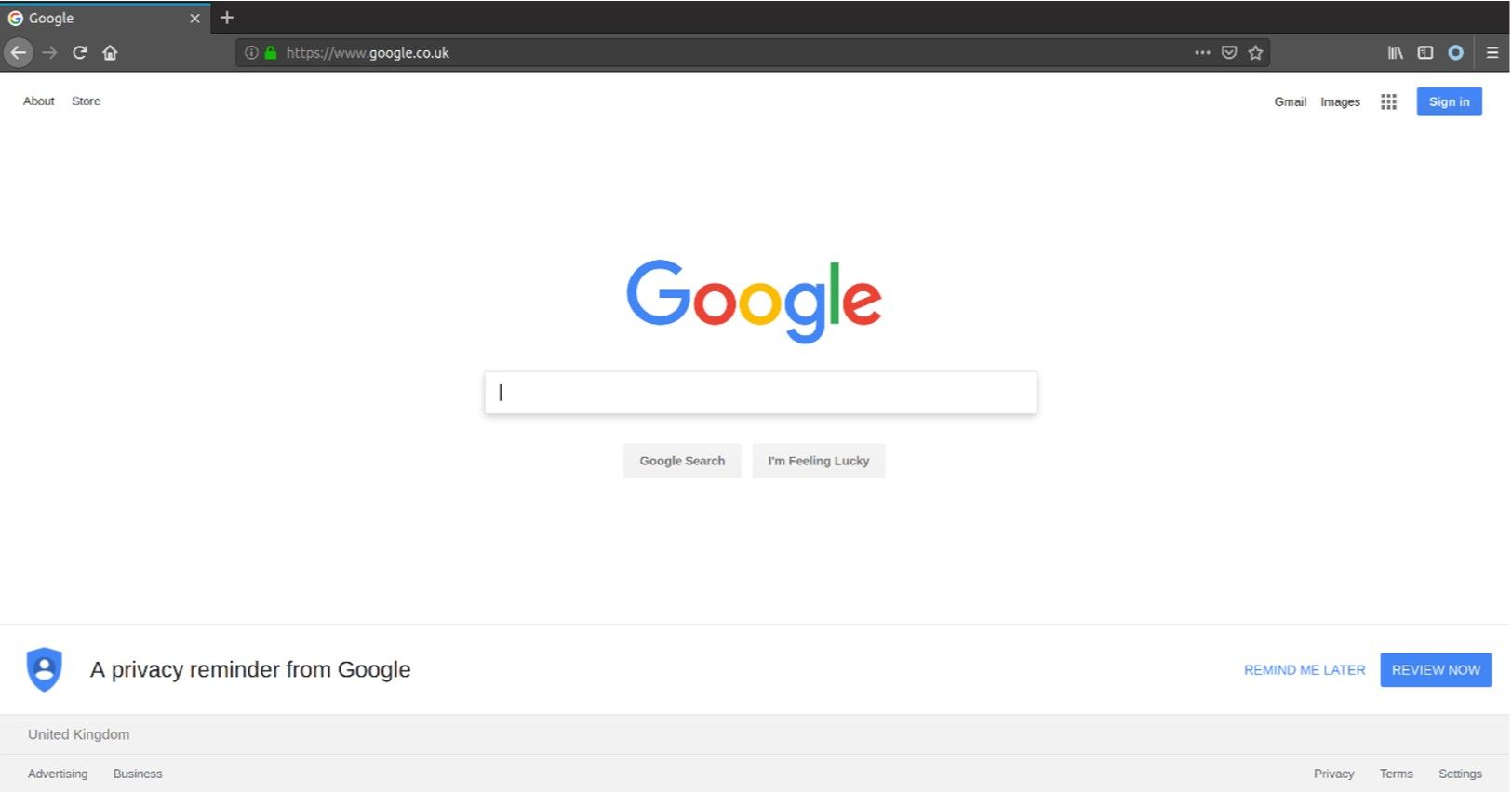
An attacker could use this for several malicious cases (not limited to):
- Load a spoofed Scottish Power login page, used to steal the login credential of the user. Since the originating URL is a valid Scottish Power URL (and has a valid certificate issued to Scottish Power), this will help strengthen the legitimacy of the attacker’s spoofed login page.
- Redirect the user to a URL which the attacker controls and downloads malware to the user’s system.
- Redirect the user to a URL which the attacker controls and injects a BeEF hook into the user’s browser before redirecting them to the original target page or even the victim’s account login page.
Resolution
The issue has now been resolved.
Vendor Notification
- 14 January 2019 - Informed vendor of identified issue. No response received.
- 11 February 2019 - Issue publicly issued based on the fact the issue has been resolved.
