Updated 17:49 3 June 2022: Added further mitigation details from Atlassian
On 2 June 2022 Atlassian published their security advisory Confluence Security Advisory 2022-06-02. Unfortunately the advisory is a for a severe vulnerability in Confluence whereby an unauthenticated attacker is able to remote execute commands on the victim Confluence server. To make matters worse, this vulnerability is being actively exploited.
Confluence is a piece of software published by Atlassian, that allows teams within organisations to be able to collaborate and produce documentation. While there is a hosted version of Confluence, there are also self-hosted solutions available.
Am I Affected?
If you are running a self-hosted version of Confluence, you will likely be affected by this vulnerability. Those using the hosted (cloud) based version of Confluence are not affected. While initially this was suspected to only affect versions 7.4.0 and later, it has been confirmed by Atlassian that this vulnerability affects ALL self-hosted versions of Confluence.
What Should I Do?
An official fix is now available. Ensure that you update to one of the versions ASAP:
- 7.4.17
- 7.13.7
- 7.14.3
- 7.15.2
- 7.16.4
- 7.17.4
- 7.18.1
Ensure that you immediately remove public (Internet) access to any self-hosted instances of Confluence. If you had any instance publicly accessible, it is highly advisable to trigger an incident response to ensure that those instances weren't successfully targeted and compromised.
If you instance was isolated (i.e. only available on a private network), the risk of a compromise remains fairly low. No further action should be required at the moment.
As an additional setup, you can configure a WAF rule to block requests that contain the characters ${ in the URL.
Atlassian have also given further mitigation guidance on their advisory. This process involves replacing jar files on the server installation. Please refer to the advisory for full instructions.
Why No Responsible Disclosure?
The issue was initially identified by the firm Veloxity, while carrying out an investigation. Given this vulnerability was being actively exploited, it makes sense, and to the credit of both firms, that an advisory was made public before the fix became available. This is to allow firms to put the appropriate measures in place to help reduce the likelihood of being successfully targeted, while the fix was being worked on.
Full details of the investigation can be found on the blog from Veloxity.
Anything Else?
Make sure that you keep look at the Altassian advisory to get up to date information, especially on the progress of the fix, as well as the steps required to implement the fix.
Further Reading
- https://confluence.atlassian.com/doc/confluence-security-advisory-2022-06-02-1130377146.html
- https://www.volexity.com/blog/2022/06/02/zero-day-exploitation-of-atlassian-confluence/
- https://blog.cloudflare.com/cloudflare-customers-are-protected-from-the-atlassian-confluence-cve-2022-26134/
- https://attackerkb.com/topics/BH1D56ZEhs/cve-2022-26134
Current Exposed Instances
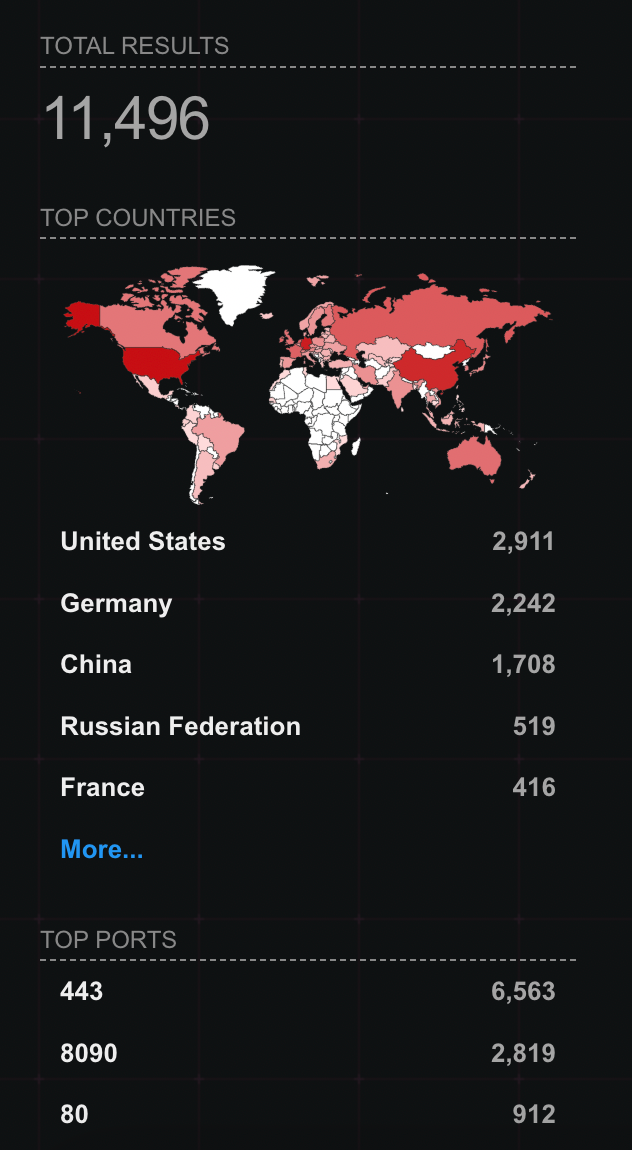
Based on a quick Shodan search, there currently appear to be around 11, 496 instances exposed to the Internet: