In this blog post I will attempt to explain HTTPS in a basic and non-technical manner. Hopefully it will server as a basic introductrion to HTTPS and some of the things to consider when you are using a HTTPS connection.
HTTP Secure
The 'S' in HTTPS stands for Secure. Thus it is a protocol used to secure HTTP connections. This includes 2 things:
- Preventing unauthorized entities from reading the data from the connection (i.e. sniffing the data being transmitted between a server and client)
- Preventing unauthorized entities from editing/manipulating the data from the connection.
Certificates
One of the backbones to the HTTPS protocol are certificates. Certificates are a means of validating the identity of some entity, be it a server, person, or even organization. There are 3 types when it comes to HTTPS connections:
- Certificate Authority certificates
- Server certificates
- Client certificates
Certificate Authority Certificates
These are also know as CA certificates. These certificates belong to Certificate Authorities (CA), entities which are responsible for issuing both server and client certificates. They are entities which one places trust into, trusting that they will only issue certificates for valid entities.
To provide some type of analogy, think of a drivers licence. The drivers licence will be a certificate, and the CA will be the government department which issues the licence. There are some security measures on the licence to show that it was the government transport department which issued the licence. If someone else issues a licence, that licence will not be trusted/valid.
Server Certificates
These certificates must always be presented by the server in a HTTPS connection. Server certificates are used by the client to validate that the server which it is connecting to, is in fact that the server which the client intended to communicate with.
Client Certificates
A server may or may not prompt for a client certificate. This is optional in the HTTPS protocol. These certificates are used by the server to validate the client which is connecting to it. When a client certificate is required by the server, this is referred to as mutual certificate authentication.
Cipher Suites
Another part of HTTPS connections are the cipher suites. I will provide a more detailed and technical explanation in a later blog post, but will attempt to provide a very brief explanation here. A cipher suite contains a collection of algorithms which will be used for the HTTPS connection. The cipher suite used is established as part of the connection handshake, where the client and server both agree upon a common cipher suite to use. The cipher suite includes the protocol used, the key exchange algorithm, the symmetric cipher (the algorithm used to perform the actual encryption of the data) and the message authentication code (the algorithm used to ensure that the data has not been tampered with). Ensuring that a sufficiently strong cipher suite is used is paramount to the security of the connection.
Certificate Errors
You will at times see errors displayed by the browser when attempting to connect to a site. It is vitally important that you do not click through these errors without first performing appropriate validation that the errors do not represent a security risk. If you are still unsure, DO NOT proceed forward. The most common errors which you will see are:
- The Certificate Authority which signed the certificate is not trusted.
- The certificates Subject Alternate Name (SAN) or Common Name (CN) do not match the hostname of the server which the client was attempting to connect to.
- The certificate has been revoked.
- The certificate has expired.
These errors could be due to a number of reasons (not limited to):
- Server misconfiguration.
- CA has been removed from the browser's trust store.
- An attacker attempting a Man in The Middle attack.
Untrusted CA
If you visit a site with a certificate signed by a CA which your browser does not trust you will get an error similar to the one below. You should not proceed forward, unless you can definitively validate that the CA is a valid and trusted CA.
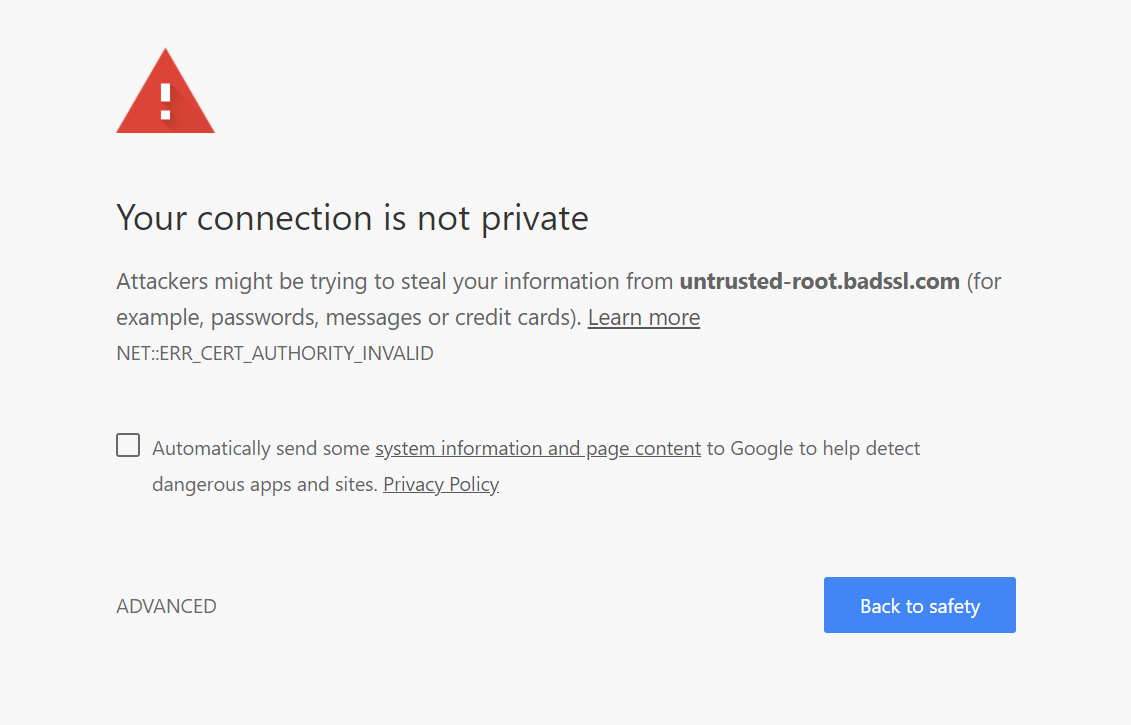
Invalid Hostname
If you visit a site where the hostname of the server which you are attempting to connect to does not match a hostname in the Subject Alternate Field (SAN) or Common Name (CN) attribute (of the Subject field), then you will be presented with an error to similar to the one below. In this case you should not proceed any further.
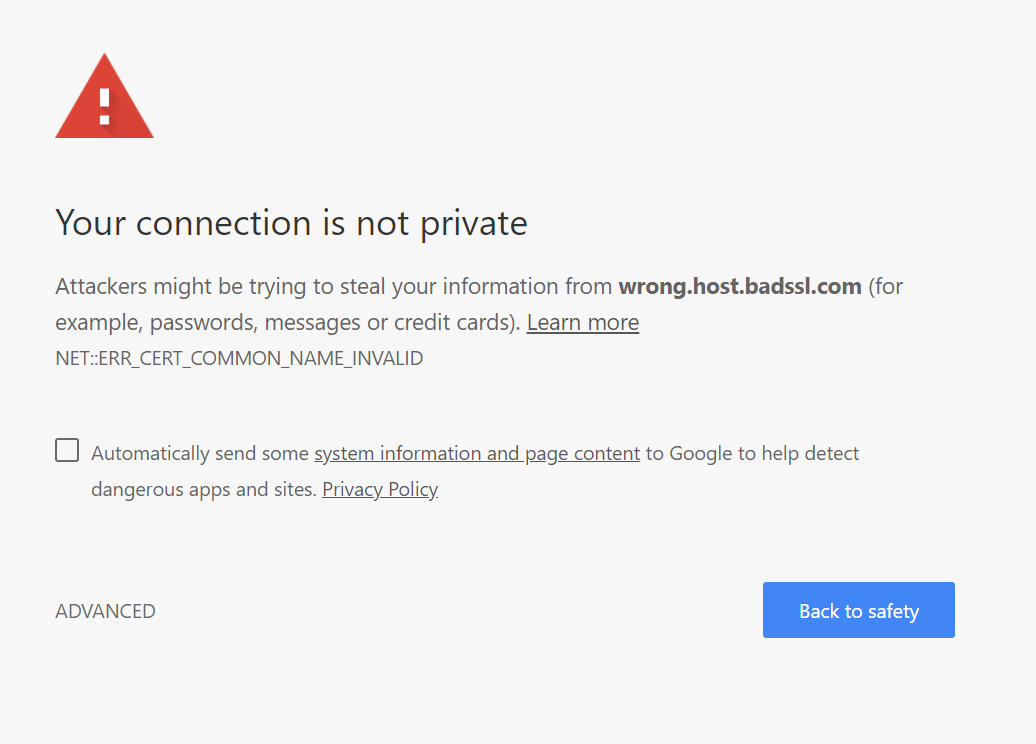
Revoked Certificate
When a certificate has been compromised, the current method is to revoke that certificate (this doesn't work as effectively as one would hope). If you attempt to visit a site which is serving a revoked certificate, you will see an error similar to the one below. Again in this case you should not proceed any further.
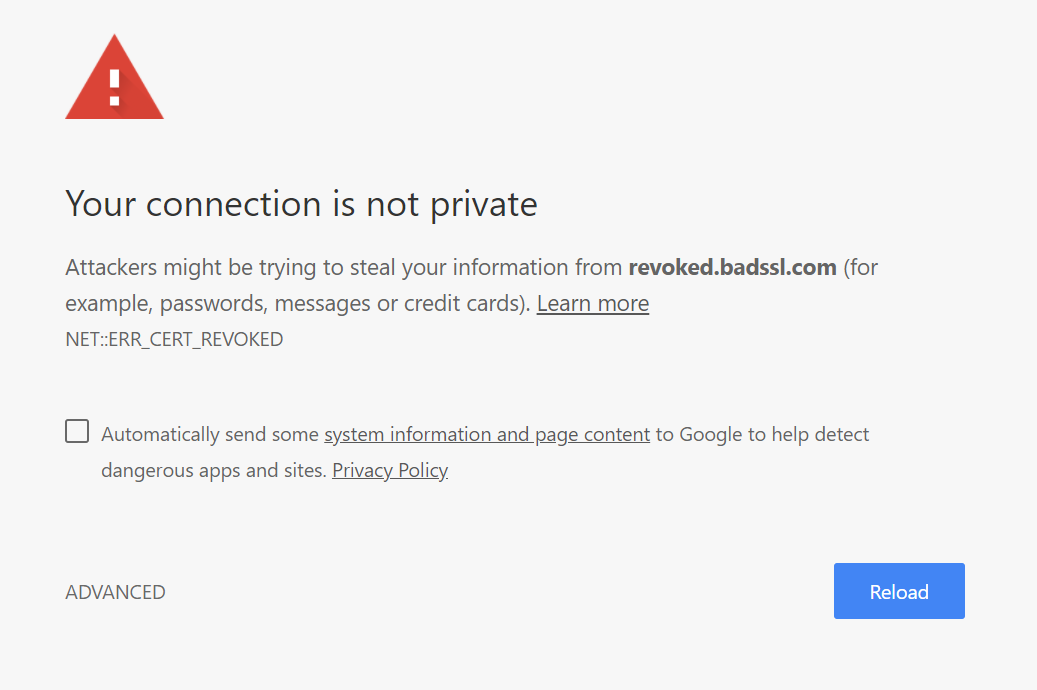
Expired Certificate
When attempting to visit a site serving an expired certificate, you will see an error similar to the one below. Generally expired certificates occur since the site owner has forgotten to renew the certificate, as well as install the new certificate on their server. If you see this, it is best to try refer to the site administrator before proceeding forward.
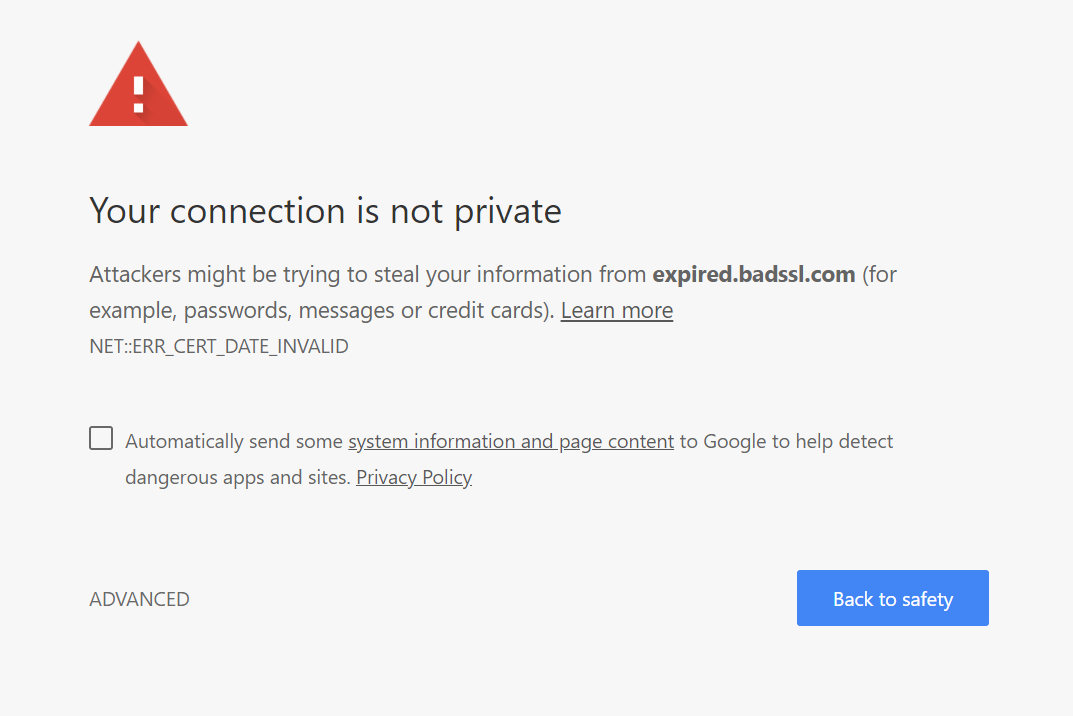
The Green Padlock
So here's the thing, the HTTPS protocol only secures the connection between 2 entities. It does not help against attacks such as phishing attempts. In fact it may even help strengthen these type of attacks, because of the past attempts of the industry to say that a green padlock means that the site is secure. Well yes it is secure, but it doesn't mean that the site is a legitimate site. The bad guys have caught onto this and now use HTTPS as means of strengthening their phishing attempts.
Take this example for PayPal:
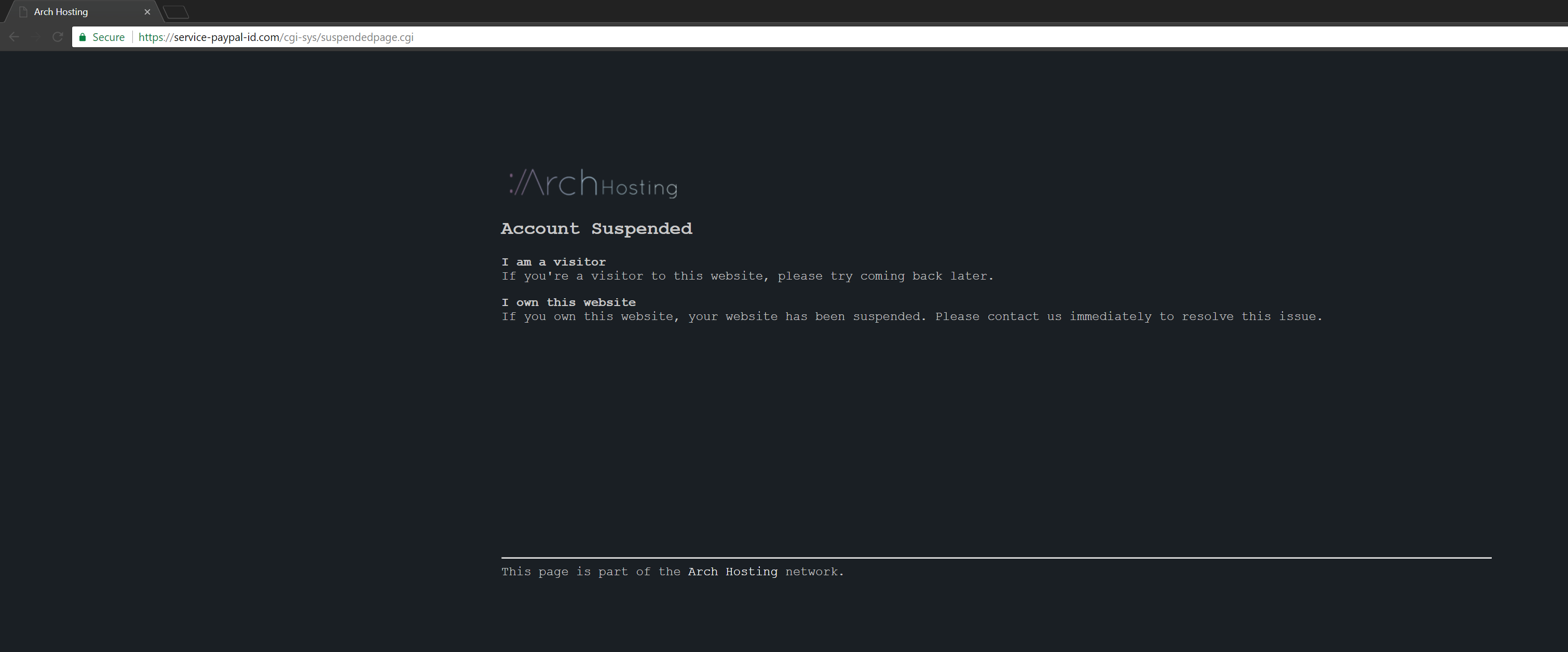
It has a green padlock. It has "paypal" in the name. It must be secure? It must be legitimate? Well yes it is secure, but as you can see the hosting company has shutdown the site, most likely due to this being a phishing site. I plan to devote another blog post explaining how one can try differentiate between legitimate sites and phishing sites.
Summary
Hopefully this has helped in some form. HTTPS is an import of the Internet today, and it continues to be adopted more and more. While it does provide a great deal of security, it is important to understand how it works to help yourself avoid some of the downsides which come along with it (such as a new and improved method of phishing).


