MFA (Multi-Factor Authentication) is the means of having multiple forms or steps required to authenticate to a service. I won't go into the details in this post since I have already covered that in another post which I wrote some time back. One form of MFA is Time-based One-time Password (TOTP). This is where an application or device derives a code which is only valid for a set period of time (typically 30 seconds).
Behind the scenes there is some cryptographic mathematics going on which generates the code so that it is only unique to the instance within the app which generates the code (so no one else can simply get the code) and only unique to your account. This happens when you config or enable MFA on your account. You will either be required to scan a QR code or enter a code which is displayed when enabling MFA on your account. When you perform this registration process is generates a secret specific to that instance, so that the code will only be valid for that specific instance (hence how it uniquely ties the code to both your account as well as your app).
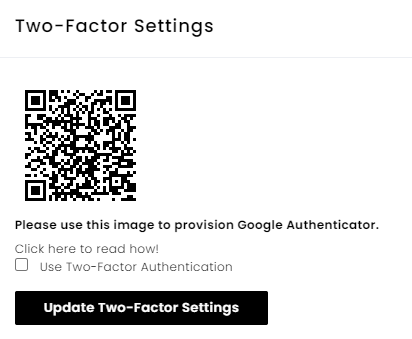
Well this is all great, you have a code which can only be generated on the app and is uniquely tied to your account. From a security perspective no one else has access to this. Well this becomes a problem when you want to upgrade to the latest shinny mobile device. Since the secret key is specific to that very instance of the TOTP registration, it means when you try setup on the a TOTP instance on your new mobile device, you have to essentially re-register MFA on your new device. This can become a rather cumbersome problem when you have multiple accounts. Also you need access to your account in order to be able to do this. Now say you lost your device, what do you do then? Your only option is to perform account recovery, which depending on the service can be very cumbersome.
In the past your only option was pretty much limited to Google's Google Authentictor app. It did the job well, but as I mentioned above, if you ever needed to move devices, it was painful and problematic. This has put a lot of people off from using TOTP and instead reverting to weaker MFA options such as Text/SMS MFA or not using MFA at all. Thankfully this has changed, and more and more TOTP apps now support backups! What this means that all your registered TOTP instances are stored within a backup (which is encrypted with a key). This means when you want to move to another device, you can restore that backup on your new device and you then have access to all your TOTP instances! There are several high profile instances out there which include Authy, Microsoft Authenticator, DUO, and Google Authenticator.
Even some password managers such as 1Password have embedded support for TOTP. Although, personally I prefer to keep my TOTP separate from my passwords, so if someone does gain access to my password manager (yes, it would be a REALLY bad day for me if that happened), they would have another hurdle to get over in order to gain access to my accounts.
Authy
Personally I use Authy, but many of the other apps which support backups function in a similar way. They save the details of your TOTP instances in an encrypted file which can then be transferred to other devices.
One of the first things you will need is to use your phone number to setup the app on your device:
Assuming that you already have an instance setup:
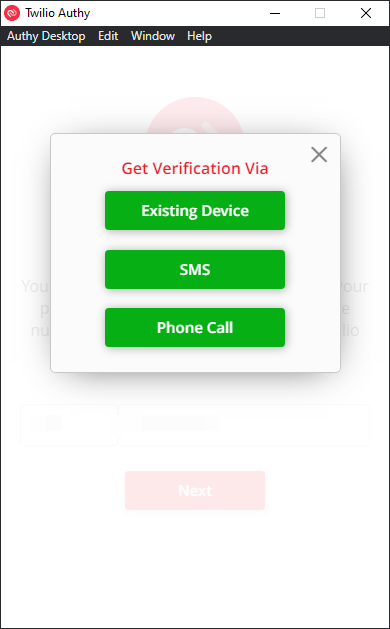
Use Existing Device and this will prompt you on the instance on your other device to allow access, you will also be required to ensure your backup password. If you have lost your device you will need use the other 2 options. You will then get a text/SMS which will then allow you to load your account:
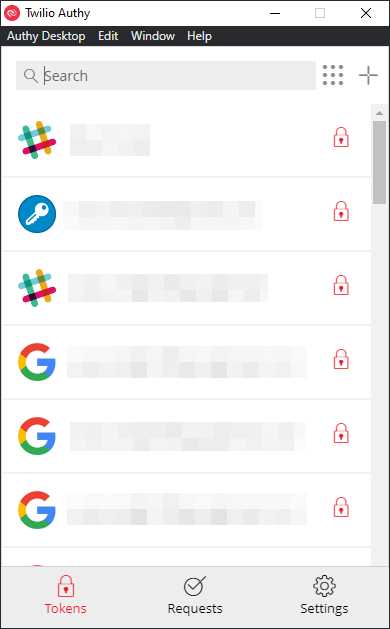
You may be thinking, IT HAS ALL MY TOKENS WITH JUST MY PHONE NUMBER!!!! That's what I initial thought. But as you will have noticed, there is a lock on the right hand-side of each entry. When you try access it you will then be prompted for your backup password:
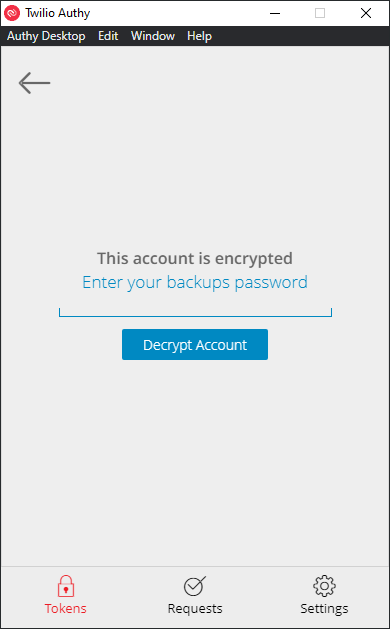
Once you have entered your backup password, the relevant information for your TOTP instance will be decrypted and you will have access to you TOTP on your new instance of Authy:

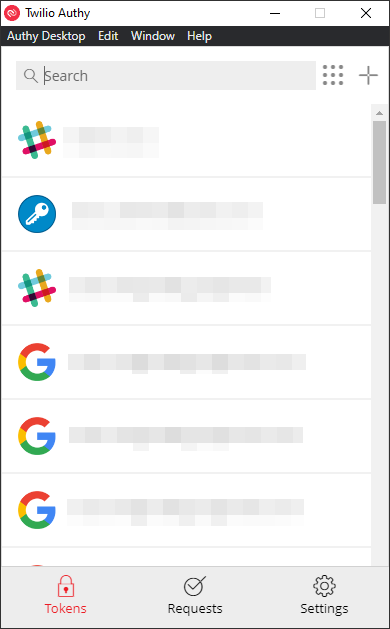
And if you go to the main screen you will have seen that the locks now no longer appear, meaning you are now able to access your other TOTP instances:
In terms of security of your account, you can monitor which devices currently have access to your account. To do this go to Settings -> Devices:
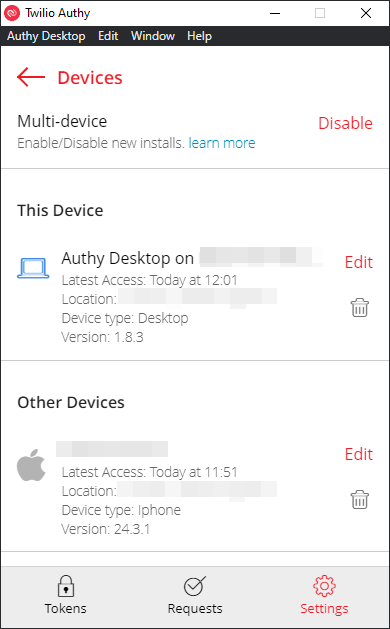
On this screen you can see which devices are active on your account as well as having the ability to remove that access. You can also restrict access to a single device (via the Multi-device option). Authy also allows you to set a pin number, as well as use your device's biometrics to restrict access to the app, which is a way to further strengthen the security of your TOTP codes.
One thing to note, access to your account is via a mobile number, so this is still vulnerable to the same attacks as SMS 2FA is. However, an attacker would still need your backup password in order to access your TOTP instances. I do however wish Authy would have a better option for this, and I might look to other alternatives such as Microsoft Authenticator, so keep an eye out for another blog post.


