Last week I wrote a blog about how I came to the decision as to why I chose Blogger as my blogging platform. I briefly mentioned that Blogger does not support TLS when using a custom domain for your blog and that one could use Cloudflare to implement TLS on your blog. This blog will provide information into some of the pitfalls of this solution as well as the numerous advantages of the solution (which could be applied to other sites).
The Basic Architecture
When using Blogger with a custom domain, without using Cloudflare, the architecture looks like:
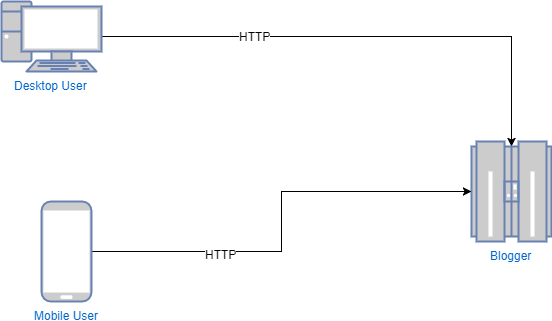
When using Blogger with a custom domain, with Cloudflare, the architecture looks like:
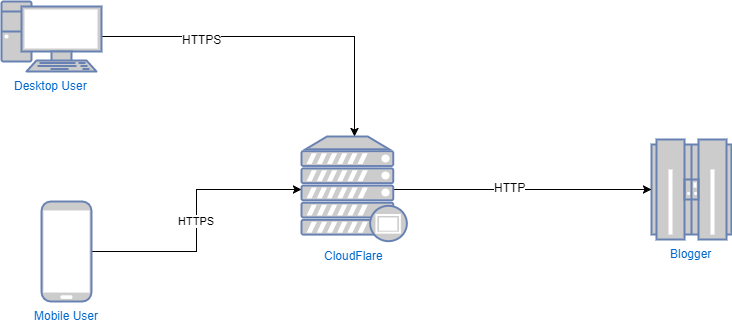
The Pitfall
One of the pitfalls is that there is still a plaintext (HTTP) connection between the Cloudflare servers and the Blogger servers. Ideally I would love to make this an encrypted (HTTPS) connection, and I have tried several techniques to try to get an encrypted connection. One attempt I had tried was to remove the custom domain and set up my domain to be an alias of the Blogger domain. I also tried to set up a load balancer on Cloudflare as well. However in both attempts I was unsuccessful. If anyone has any ideas, please leave them in the comments below. I would love to hear your ideas.
I’ve since reluctantly come to admit defeat and live with the risk for now. I’ve decided that the risk is so low, that it would be acceptable at the beginnings of a blog. Hopefully Google will implement TLS for custom domains on Blogger soon. Otherwise I shall look to move onto a new platform in the not too distant future. Coming back to the risk, in order for someone to effectively exploit this, they would have to Man in The Middle (MiTM) the connection between the Cloudflare servers and the Blogger servers. This is an extremely unlikely scenario. However ordinary users, who would be more likely to face being Man in The Middle’d (via attacks such as the recent KRACK attack), will be protected as their connection to the Cloudflare servers will be encrypted with TLS.
The Benefits
There are several benefits of using Cloudflare. When one typically uses a hosted service, they have little to no control over what headers or security related controls they can enable (such as HSTS, redirects from HTTP to HTTPS, etc). By placing Cloudflare in front of these hosted services, it allows you to enable these security related enhancements. I will take you through a few which I enabled for my blog:
Always Use HTTPS
With this option set to on, all connections through Cloudflare will automatically redirect all plaintext (HTTP) connections to HTTPS connections.
HTTP Strict Transport Security (HSTS)
With this option set, Cloudflare will add the HSTS header to all HTTPS connections made through Cloudflare. In addition one has the ability to customize every component of this header which includes:
- Maximum age
- Include subdomains
- Preload
- No-sniff
Authenticated Origin Pulls
This option allows you to cryptographically verify that all requests made to the Blogger server have been made by the CloudFlare servers. This will further help prevent Man in The Middle attacks between the CloudFlare and Blogger servers. This also helps prevents users from navigating directly to the Blogger servers (thereby bypassing some of the security protections which have been put in place by CloudFlare).
Opportunistic Encryption
This option provides support for HTTP/2 and SPDY.
TLS1.3
This option allows support for the new TLS 1.3 protocol.
Automatic HTTPS Rewrite
This helps prevent mixed content (where plain HTTP requests are made from a page which has loaded over HTTPS, such as static content). With this option set, CloudFlare will help rewrite HTTP resources to ensure that they are fetched over HTTPS. CloudFlare uses data from EFF’s HTTP Everywhere as well as Chrome’s HSTS preload list, to determine which items to rewrite. CloudFlare will perform the rewrite only if the resource can be loaded over HTTPS.
Conclusion
As can be seen from above CloudFlare is a fantastic tool. Which can be used as a great aid to help strengthen the overall security of your site. It has many other features such as WAF, Caching, and DOS protection. Some of these are free and others require one of their paid tiers to access the feature. However for a basic blog, their free account has more than enough features to get you going, I highly recommend that you at least have a look at it.


