Let me start off by stating that this is by no means a criticism of Certificate Transparency. I think that it is a great idea, and is an invaluable tool.
What is Certificate Transparency?
Certificate Transparency (CT) is an open source framework used by Certificate Authorities (CA) as a means to audit and monitor certificates which they issue. This is accomplished through a system of logs, auditors and monitors. The concept around this framework is to allow domain owners to identify which certificates have been issued against their domain, allowing them to be able to identify certificates which have been issued either maliciously or accidentally. From April 2018, Chrome will require that all publicly trusted certificates were issued by a CA using CT.
Certificate Transparency Monitoring Tools
There are several tools out there which you can use to help monitor certificates which have been issued under your domain:
- Facebook has an excellent tool, which alerts you to when a new certificate has been issued on the domains which you set it to monitor and alert on.
- Certstream introduces an interesting concept to CT. This service attempts to provide real-time logs which one can stream.
- Censys is a search engine which allows one to search for hosts and networks which are open on the Internet. In addition it also incorporates CT logs to allow one to search for certificates as well.
Certificate Transparency, a Peek Into The Inside
Since all certificates issued by the CA result in the details of that certificate being audited and logged, all certificates issued by that CA are publicly visible and searchable through CT tools and logs. And here-in lies the problem. For publicly accessible sites, this is to be expected. They are open on the Internet after all. However for systems which are only accessible via a local or corporate network, this results in information leakage. Using tools such as Censys, an attacker can search for all certificates issued to a specific organisation:
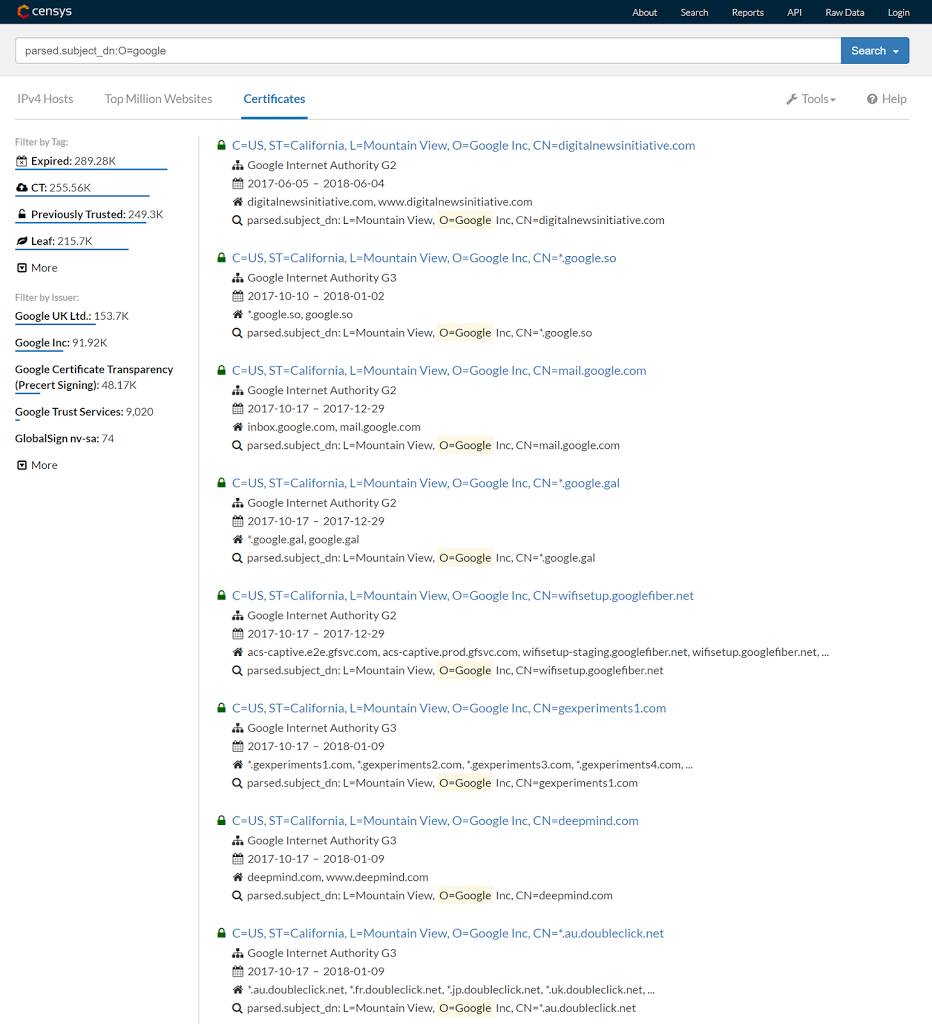
So CT becomes another useful tool which an attacker can add to their arsenal to help aid in their footprinting of an organisation. Since the attacker never hits the target network, this activity raises no suspicions either. This might not be a treasure trove for an attacker, but it is another piece of information which an attacker might have not been able to get their hands on before. Any piece of information, no matter how small, can and will be used by attackers, especially if it takes little effort on their behalf to obtain it.
The only effective means to combat this, is for the organisation to stand up their own CA and issue their own certificates for internal systems. However this can be quite complex and comes with it’s own set of challenges, so often might not be worth the effort (especially for smaller organisations). However for those organisations with their own internal PKI infrastructure, internally facing systems should rather user certificates issued internally rather than by a public CA. This also has the added benefit of possibly reducing costs, since internally signed certificates should not carry any cost (whereas most public CA’s charge a fee for generating a certificate).

